1. Pengantar
Grup Endpoint Jaringan (NEG) Private Service Connect (PSC) mendukung perantaian Load Balancer HTTPS Internal dengan Load Balancer HTTPS Eksternal. Solusi ini menyediakan Pemeriksaan Kesehatan Terdistribusi dan traffic bidang Data ke Lokal menggunakan rentang yang ditentukan pelanggan. Selain itu, beberapa VPC yang terhubung ke Lokal melalui beberapa InterConnect regional juga didukung dengan topologi ini.
Dalam codelab ini, kami akan menunjukkan cara mengonfigurasi ini secara menyeluruh berdasarkan topologi di bawah. Dari kiri ke kanan, pelanggan lokal memiliki VM untuk menyimulasikan layanan HTTP, memanfaatkan konektivitas hybrid (HA-VPN atau InterConnect), dan NEG hybrid untuk mengekspos melalui load balancer HTTPS Internal. PSC menggunakan LB HTTPS Internal sebagai lampiran layanan. NEG PSC menggunakan lampiran sebagai layanan backend, yang diekspos ke LB HTTPS Eksternal. Pengguna internet dapat menggunakan jaringan global Google untuk mempercepat akses layanan HTTP Lokal.
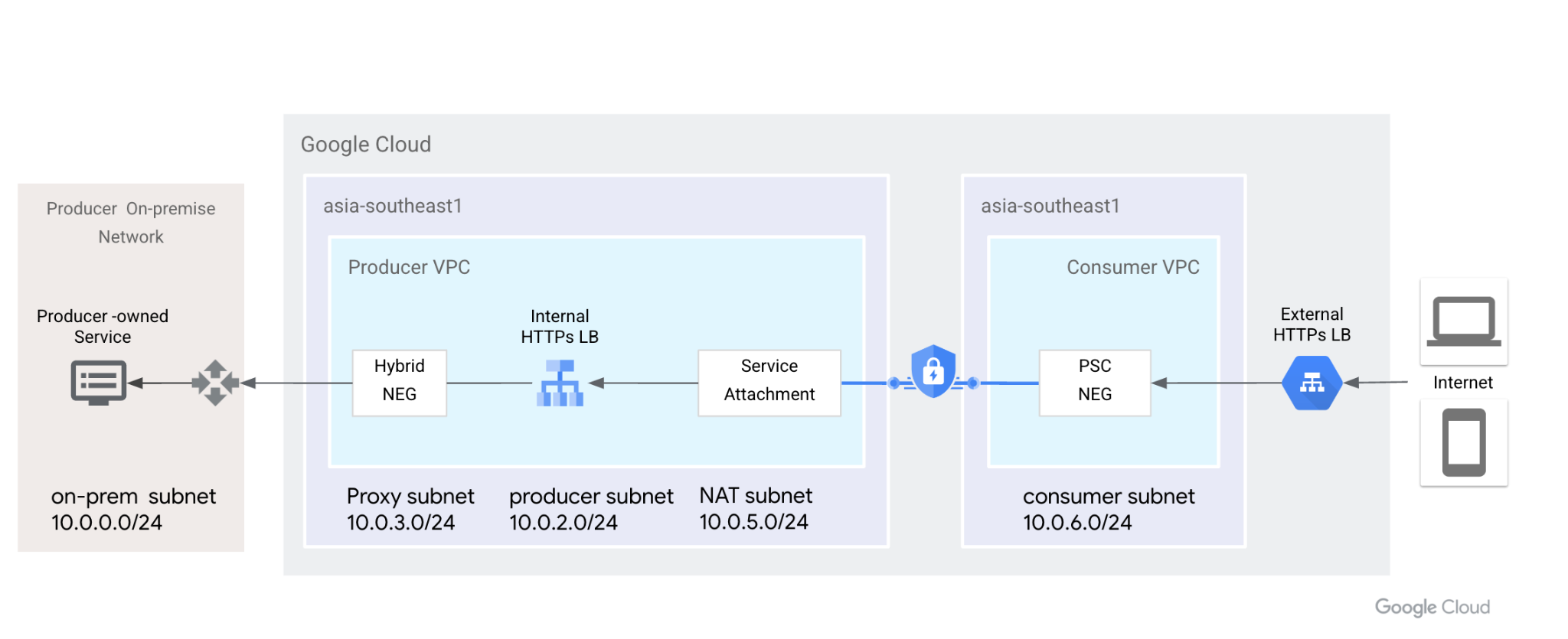
Gambar 1. Private Service Connect menggunakan Network Endpoint Group dan lampiran layanan untuk menghubungkan Load Balancer HTTPS Eksternal ke Load Balancer HTTPS Internal, dan memperluas backend ke On-Prem.
Yang akan Anda pelajari
- Load Balancer HTTPS Internal dengan NEG Hybrid dan Health Check Terdistribusi
- Lampiran Layanan PSC dengan Load Balancer HTTPS Internal
- Penyiapan Grup Endpoint Jaringan PSC
- Mengekspos NEG PSC dengan Load Balancer HTTPS Eksternal
Yang Anda butuhkan
- Pengetahuan tentang Konektivitas Hybrid, seperti HA-VPN
- Pengetahuan tentang Load Balancing HTTPS Internal/Eksternal
- Pengetahuan tentang Private Service Connect
2. Sebelum memulai
Catatan: Codelab menawarkan langkah-langkah konfigurasi dan validasi berdasarkan topologi yang diilustrasikan, ubah prosedur sesuai kebutuhan organisasi Anda. Izin IAM tidak termasuk dalam cakupan codelab.
Codelab akan menggunakan satu project untuk menyimulasikan seluruh proses. Beberapa project juga didukung.
Project Tunggal - Memperbarui project untuk mendukung jaringan produsen dan konsumen
Di dalam Cloud Shell, pastikan project ID Anda sudah disiapkan
gcloud config list project gcloud config set project [YOUR-PROJECT-NAME] prodproject=YOUR-PROJECT-NAME echo $prodproject
3. Buat Resource Lokal
Di bagian berikut, kita akan menyiapkan VPC dan VM lokal untuk menyimulasikan layanan lokal pelanggan.
Jaringan VPC
Dari Cloud Shell
gcloud compute networks create vpc-demo-onprem --project=$prodproject --subnet-mode=custom
Buat Subnet
Dari Cloud Shell
gcloud compute networks subnets create vpc-demo-onprem-asia-southeast1 --project=$prodproject --range=10.0.0.0/24 --network=vpc-demo-onprem --region=asia-southeast1
Buat aturan Firewall.
Load Balancer HTTPS Internal mendukung health check terdistribusi, aturan firewall hanya perlu mengizinkan rentang IP subnet proxy. Mengikuti dokumen untuk mengizinkan project Anda.
Dari Cloud Shell, buat aturan firewall untuk mengaktifkan health check backend dan traffic bidang data dari subnet proxy.
gcloud compute firewall-rules create vpc-demo-health-checks --allow tcp:80,tcp:443 --network vpc-demo-onprem --source-ranges 10.0.3.0/24 --enable-logging
Dari Cloud Shell, buat aturan firewall untuk mengizinkan IAP terhubung ke instance VM Anda,
gcloud compute firewall-rules create psclab-iap-prod --network vpc-demo-onprem --allow tcp:22 --source-ranges=35.235.240.0/20 --enable-logging
4. Membuat Instance VM Lokal
VM ini menyimulasikan layanan lokal, dan harus diekspos dengan Load Balancer HTTPS Internal menggunakan NEG campuran.
Dari Cloud Shell, buat instance www01
gcloud compute instances create www01 \
--zone=asia-southeast1-b \
--image-family=debian-11 \
--image-project=debian-cloud \
--network-interface=network-tier=PREMIUM,nic-type=GVNIC,stack-type=IPV4_ONLY,subnet=vpc-demo-onprem-asia-southeast1 \
--shielded-secure-boot \
--shielded-vtpm \
--shielded-integrity-monitoring \
--metadata=startup-script='#! /bin/bash
sudo apt-get update
sudo apt-get install nginx -y
vm_hostname="$(curl -H "Metadata-Flavor:Google" \
http://169.254.169.254/computeMetadata/v1/instance/name)"
filter="{print \$NF}"
vm_zone="$(curl -H "Metadata-Flavor:Google" \
http://169.254.169.254/computeMetadata/v1/instance/zone \
| awk -F/ "${filter}")"
echo "Page on $vm_hostname in $vm_zone" | \
tee /var/www/html/index.nginx-debian.html
sudo systemctl restart nginx'
Di bagian berikut, kita akan menggunakan letsencrypt untuk membuat sertifikat dan menginstal di Nginx. Download file kunci publik dan pribadi untuk langkah berikutnya. Anda perlu membuka sementara port TCP 80 ke Internet untuk pembuatan sertifikat.
Pastikan VM ini memiliki nama domain yang diselesaikan secara publik. Misalnya, di Cloud DNS, tambahkan data A [www01.yinghli.demo.altostrat.com](http://www01.yinghli.demo.altostrat.com) dan arahkan ke alamat IP publik VM.
gcloud dns --project=$prodproject record-sets create www01.yinghli.demo.altostrat.com. --zone="yinghli-demo" --type="A" --ttl="300" --rrdatas="34.87.77.186"
Dari konsol VM www01, ikuti panduan untuk menginstal sertifikat di Nginx dan buat salinan fullchain.pem dan private.pem untuk langkah-langkah berikut.
sudo apt install snapd sudo snap install core; sudo snap refresh core sudo snap install --classic certbot sudo ln -s /snap/bin/certbot /usr/bin/certbot sudo certbot --nginx
5. Membuat jaringan VPC Produser
Catatan: Konfigurasi jaringan hybrid TIDAK disertakan dalam konfigurasi ini.
Jaringan VPC
Dari Cloud Shell
gcloud compute networks create vpc-demo-producer --project=$prodproject --subnet-mode=custom
Buat Subnet
Dari Cloud Shell
gcloud compute networks subnets create vpc-demo-asia-southeast1 --project=$prodproject --range=10.0.2.0/24 --network=vpc-demo-producer --region=asia-southeast1
Buat Subnet Proxy
Dari Cloud Shell
gcloud compute networks subnets create proxy-subnet-asia-southeast1 \ --purpose=REGIONAL_MANAGED_PROXY \ --role=ACTIVE \ --region=asia-southeast1 \ --network=vpc-demo-producer \ --range=10.0.3.0/24
Konektivitas Hybrid
Ikuti dokumentasi Cloud VPN untuk mengimplementasikan konektivitas VPN dengan ketersediaan tinggi (HA) antara VPC Lokal dan Produsen. Pertahankan konfigurasi default pada Cloud Router, kita tidak perlu menambahkan 130.211.0.0/22, 35.191.0.0/16 ke dalam iklan BGP.
6. Buat NEG Campuran Produsen
Buat grup endpoint jaringan hybrid dan tambahkan VM lokal IP:PORT ke NEG.
Dari Cloud Shell
gcloud compute network-endpoint-groups create on-prem-service-neg \
--network-endpoint-type=NON_GCP_PRIVATE_IP_PORT \
--zone=asia-southeast1-b \
--network=vpc-demo-producer
gcloud compute network-endpoint-groups update on-prem-service-neg \
--zone=asia-southeast1-b \
--add-endpoint="ip=10.0.0.2,port=443"
7. Membuat Load Balancer HTTPS Internal Produsen
Saat ini Load Balancer HTTPS Eksternal hanya mendukung protokol HTTPS untuk NEG PSC( dokumen). Saat memublikasikan layanan, kita perlu menggunakan Load Balancer HTTPS Internal dan mengaktifkan akses global aturan penerusan.
Dari Cloud Shell, buat health check regional.
gcloud compute health-checks create https on-prem-service-hc \
--region=asia-southeast1 \
--use-serving-port
Dari Cloud Shell, buat layanan backend dan tambahkan NEG Hybrid.
gcloud compute backend-services create on-premise-service-backend \ --load-balancing-scheme=INTERNAL_MANAGED \ --protocol=HTTPS \ --region=asia-southeast1 \ --health-checks=on-prem-service-hc \ --health-checks-region=asia-southeast1 gcloud compute backend-services add-backend on-premise-service-backend \ --network-endpoint-group=on-prem-service-neg \ --network-endpoint-group-zone=asia-southeast1-b \ --region=asia-southeast1 \ --balancing-mode=RATE \ --max-rate-per-endpoint=100
Dari Cloud Shell, buat peta URL
gcloud compute url-maps create on-premise-url \
--default-service on-premise-service-backend \
--region=asia-southeast1
Dari Cloud Shell, buat sertifikat SSL regional. Dua file sertifikat didownload dari VM.
gcloud compute ssl-certificates create www01 \
--certificate=fullchain.pem \
--private-key=private.pem \
--region=asia-southeast1
Dari Cloud Shell, buat https-target-proxy
gcloud compute target-https-proxies create on-premise-httpsproxy \
--ssl-certificates=www01 \
--url-map=on-premise-url \
--url-map-region=asia-southeast1 \
--region=asia-southeast1
Cadangkan IP statis internal dari Cloud Shell dan buat aturan penerusan
gcloud compute addresses create ilbaddress \
--region=asia-southeast1 \
--subnet=vpc-demo-asia-southeast1 \
--addresses=10.0.2.100
gcloud compute forwarding-rules create https-ilb-psc \
--load-balancing-scheme=INTERNAL_MANAGED \
--network=vpc-demo-producer \
--subnet=vpc-demo-asia-southeast1 \
--address=ilbaddress \
--ports=443 \
--region=asia-southeast1 \
--target-https-proxy=on-premise-httpsproxy \
--target-https-proxy-region=asia-southeast1
--allow-global-access
8. Membuat instance Producer VM
Buat VM produser untuk verifikasi.
Dari Cloud Shell
gcloud compute instances create test01 \
--zone=asia-southeast1-b \
--image-family=debian-11 \
--image-project=debian-cloud \
--network-interface=network-tier=PREMIUM,nic-type=GVNIC,stack-type=IPV4_ONLY,subnet=vpc-demo-asia-southeast1 \
--shielded-secure-boot \
--shielded-vtpm \
--shielded-integrity-monitoring
Agar IAP dapat terhubung ke instance VM Anda, buat aturan firewall yang:
Dari Cloud Shell
gcloud compute firewall-rules create psclab-iap-prod --network vpc-demo-producer --allow tcp:22 --source-ranges=35.235.240.0/20 --enable-logging
Dari konsol VM produsen, akses [www01.yinghli.demo.altostrat.com](https://www01.yinghli.demo.altostrat.com) dan tentukan alamat IP load balancer HTTPS Internal. HTTP 200 menunjukkan bahwa konfigurasi berfungsi seperti yang diharapkan.
curl -v --resolve www01.yinghli.demo.altostrat.com:443:10.0.2.100 https://www01.yinghli.demo.altostrat.com * Added www01.yinghli.demo.altostrat.com:443:10.0.2.100 to DNS cache * Hostname www01.yinghli.demo.altostrat.com was found in DNS cache * Trying 10.0.2.100:443... * Connected to www01.yinghli.demo.altostrat.com (10.0.2.100) port 443 (#0) * ALPN, offering h2 * ALPN, offering http/1.1 * successfully set certificate verify locations: * CAfile: /etc/ssl/certs/ca-certificates.crt * CApath: /etc/ssl/certs * TLSv1.3 (OUT), TLS handshake, Client hello (1): * TLSv1.3 (IN), TLS handshake, Server hello (2): * TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8): * TLSv1.3 (IN), TLS handshake, Certificate (11): * TLSv1.3 (IN), TLS handshake, CERT verify (15): * TLSv1.3 (IN), TLS handshake, Finished (20): * TLSv1.3 (OUT), TLS change cipher, Change cipher spec (1): * TLSv1.3 (OUT), TLS handshake, Finished (20): * SSL connection using TLSv1.3 / TLS_AES_256_GCM_SHA384 * ALPN, server accepted to use h2 * Server certificate: * subject: CN=www01.yinghli.demo.altostrat.com * start date: Jun 4 10:36:43 2023 GMT * expire date: Sep 2 10:36:42 2023 GMT * subjectAltName: host "www01.yinghli.demo.altostrat.com" matched cert's "www01.yinghli.demo.altostrat.com" * issuer: C=US; O=Let's Encrypt; CN=R3 * SSL certificate verify ok. * Using HTTP2, server supports multi-use * Connection state changed (HTTP/2 confirmed) * Copying HTTP/2 data in stream buffer to connection buffer after upgrade: len=0 * Using Stream ID: 1 (easy handle 0x55865ef982e0) > GET / HTTP/2 > Host: www01.yinghli.demo.altostrat.com > user-agent: curl/7.74.0 > accept: */* > * TLSv1.3 (IN), TLS handshake, Newsession Ticket (4): * TLSv1.3 (IN), TLS handshake, Newsession Ticket (4): * old SSL session ID is stale, removing * Connection state changed (MAX_CONCURRENT_STREAMS == 100)! < HTTP/2 200 < server: nginx/1.18.0 < date: Mon, 05 Jun 2023 02:29:38 GMT < content-type: text/html < content-length: 35 < last-modified: Sun, 04 Jun 2023 09:02:16 GMT < etag: "647c5318-23" < accept-ranges: bytes < via: 1.1 google < Page on www01 in asia-southeast1-b * Connection #0 to host www01.yinghli.demo.altostrat.com left intact
Catatan: Anda tidak dapat mengakses layanan HTTPS VM 10.0.0.2 secara langsung karena firewall lokal hanya mengizinkan akses subnet proxy 10.0.3.0/24.
9. Buat subnet NAT PSC
Dari Cloud Shell
gcloud compute networks subnets create psc-nat-subnet \ --network=vpc-demo-producer \ --region=asia-southeast1 \ --range=10.0.5.0/24 \ --purpose=private-service-connect
10. Membuat lampiran layanan HTTPs
Dari Cloud Shell, buat lampiran layanan HTTPs
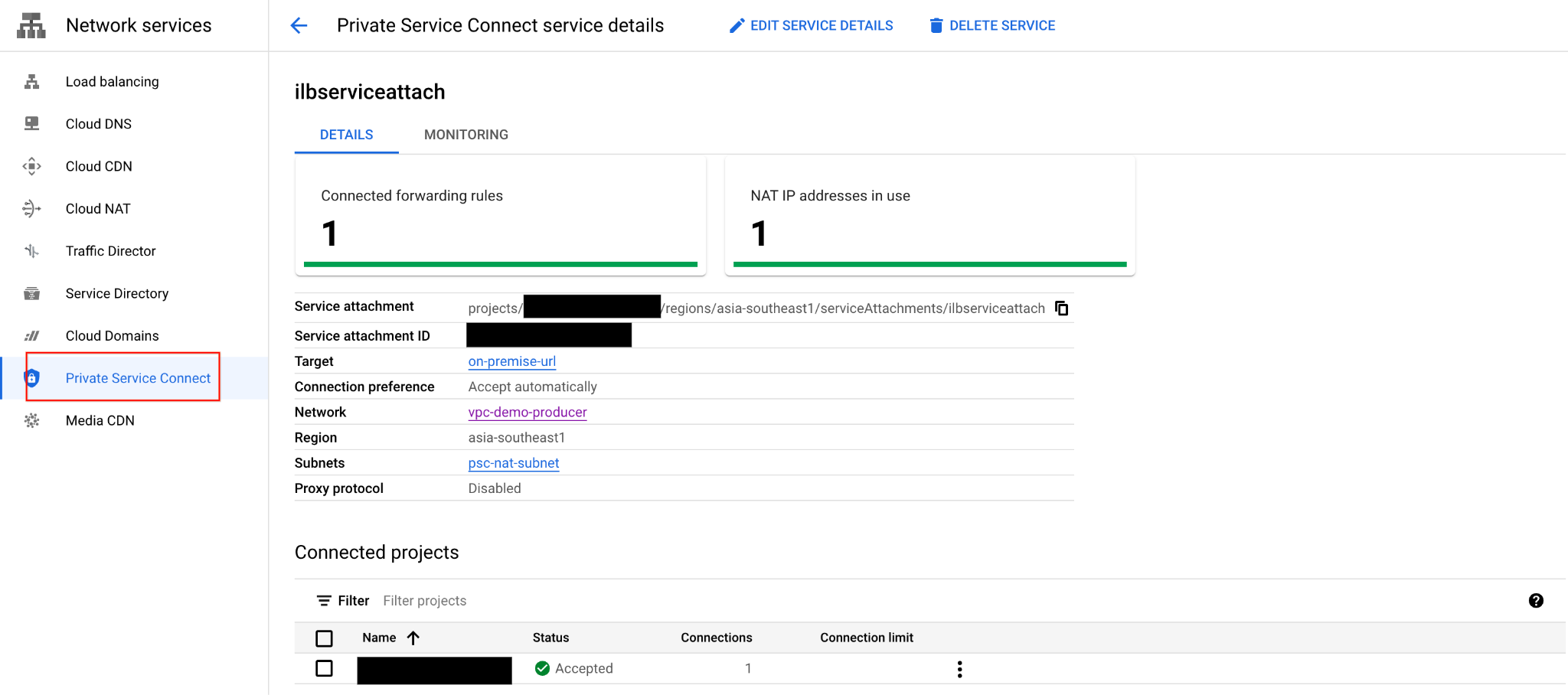
gcloud compute service-attachments create ilbserviceattach \ --region=asia-southeast1 \ --producer-forwarding-rule=https-ilb-psc \ --connection-preference=ACCEPT_AUTOMATIC \ --nat-subnets=psc-nat-subnet
Memvalidasi lampiran layanan HTTPs
gcloud compute service-attachments describe ilbserviceattach --region asia-southeast1
Nama lampiran layanan kumpulan data:
projects/<project>/regions/asia-southeast1/serviceAttachments/ilbserviceattach
11. Membuat jaringan VPC Konsumen
Di bagian berikut, VPC konsumen dikonfigurasi dalam project yang sama, tetapi project yang berbeda juga didukung. Komunikasi antara jaringan konsumen dan produsen dilakukan melalui lampiran layanan yang didefinisikan dalam jaringan produsen.
Jaringan VPC
Dari Cloud Shell
gcloud compute networks create vpc-demo-consumer --project=$prodproject --subnet-mode=custom
Buat Subnet
Dari Cloud Shell
gcloud compute networks subnets create consumer-subnet --project=$prodproject --range=10.0.6.0/24 --network=vpc-demo-consumer --region=asia-southeast1
12. Buat Grup Endpoint Jaringan PSC
Buat NEG PSC
Salin nama lampiran layanan https sebelumnya, lalu tempel di parameter --psc-target-service
Dari Cloud Shell
gcloud beta compute network-endpoint-groups create consumerpscneg \ --project=$prodproject \ --region=asia-southeast1 \ --network-endpoint-type=PRIVATE_SERVICE_CONNECT \ --psc-target-service=projects/<project>/regions/asia-southeast1/serviceAttachments/ilbserviceattach \ --network=vpc-demo-consumer \ --subnet=consumer-subnet
Setelah penyiapan NEG PSC berhasil, dari UI, ikuti Private Service Connect -> Published Services -> Perhatikan bahwa koneksi ilbserviceattach yang dipublikasikan kini menunjukkan 1 aturan penerusan.
13. Membuat Load Balancer HTTPS Eksternal Konsumen
Buat Load Balancer HTTPS Eksternal dan gunakan NEG PSC sebagai layanan backend( dokumentasi).
Dari Cloud Shell
gcloud compute addresses create httpspsclb \
--ip-version=IPV4 --global
gcloud compute backend-services create consumer-bs \
--load-balancing-scheme=EXTERNAL_MANAGED \
--protocol=HTTPS \
--global
gcloud compute backend-services add-backend consumer-bs \
--network-endpoint-group=consumerpscneg \
--network-endpoint-group-region=asia-southeast1 \
--global
gcloud compute url-maps create consumer-url \
--default-service=consumer-backend-service \
--global
gcloud compute ssl-certificates create wwwglobal \
--certificate=fullchain.pem \
--private-key=private.pem \
--global
gcloud compute target-https-proxies create consumer-url-target-proxy \
--url-map=consumer-url \
--ssl-certificates=wwwglobal
gcloud compute forwarding-rules create consumer-url-forwarding-rule \
--load-balancing-scheme=EXTERNAL_MANAGED \
--network-tier=PREMIUM \
--address=httpspsclb \
--target-https-proxy=consumer-url-target-proxy \
--ports=443 \
--global
Perbarui data DNS untuk www01.yinghli.demo.altostrat.com dan arahkan kursor ke alamat IP publik Load Balancer HTTPS Eksternal
gcloud dns --project=$prodproject record-sets update www01.yinghli.demo.altostrat.com. --type="A" --zone="yinghli-demo" --rrdatas="34.102.178.214" --ttl="300"
14. Validasi
Dari laptop, akses https://www01.yinghli.demo.altostrat.com dengan curl.
curl -v https://www01.yinghli.demo.altostrat.com * Trying 34.102.178.214:443... * Connected to www01.yinghli.demo.altostrat.com (34.102.178.214) port 443 (#0) * ALPN: offers h2,http/1.1 * TLSv1.3 (OUT), TLS handshake, Client hello (1): * TLSv1.3 (IN), TLS handshake, Server hello (2): * TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8): * TLSv1.3 (IN), TLS handshake, Certificate (11): * TLSv1.3 (IN), TLS handshake, CERT verify (15): * TLSv1.3 (IN), TLS handshake, Finished (20): * TLSv1.3 (OUT), TLS change cipher, Change cipher spec (1): * TLSv1.3 (OUT), TLS handshake, Finished (20): * SSL connection using TLSv1.3 / TLS_AES_256_GCM_SHA384 * ALPN: server accepted h2 * Server certificate: * subject: CN=www01.yinghli.demo.altostrat.com * start date: Jun 4 10:36:43 2023 GMT * expire date: Sep 2 10:36:42 2023 GMT * subjectAltName: host "www01.yinghli.demo.altostrat.com" matched cert's "www01.yinghli.demo.altostrat.com" * issuer: C=US; O=Let's Encrypt; CN=R3 * SSL certificate verify ok. * using HTTP/2 * h2h3 [:method: GET] * h2h3 [:path: /] * h2h3 [:scheme: https] * h2h3 [:authority: www01.yinghli.demo.altostrat.com] * h2h3 [user-agent: curl/8.0.0] * h2h3 [accept: */*] * Using Stream ID: 1 (easy handle 0x149019a00) > GET / HTTP/2 > Host: www01.yinghli.demo.altostrat.com > user-agent: curl/8.0.0 > accept: */* > * TLSv1.3 (IN), TLS handshake, Newsession Ticket (4): * TLSv1.3 (IN), TLS handshake, Newsession Ticket (4): * old SSL session ID is stale, removing < HTTP/2 200 < server: nginx/1.18.0 < date: Mon, 05 Jun 2023 02:48:43 GMT < content-type: text/html < content-length: 35 < last-modified: Sun, 04 Jun 2023 09:02:16 GMT < etag: "647c5318-23" < accept-ranges: bytes < via: 1.1 google, 1.1 google < alt-svc: h3=":443"; ma=2592000,h3-29=":443"; ma=2592000 < Page on www01 in asia-southeast1-b * Connection #0 to host www01.yinghli.demo.altostrat.com left intact
15. Langkah-langkah pembersihan
Langkah-langkah pembersihan jaringan produsen
Catatan: Langkah-langkah pembersihan hanya menampilkan Load Balancer dan konfigurasi terkait PSC. VPC dan Konektivitas Hybrid tidak termasuk.
Dari satu Cloud Shell di terminal, hapus komponen lab
gcloud compute forwarding-rules delete consumer-url-forwarding-rule --global gcloud compute target-https-proxies delete consumer-url-target-proxy gcloud compute ssl-certificates delete wwwglobal --global gcloud compute url-maps delete consumer-url gcloud compute backend-services delete consumer-bs --global gcloud compute addresses delete httpspsclb --global gcloud beta compute network-endpoint-groups delete consumerpscneg --region=asia-southeast1 gcloud compute service-attachments delete ilbserviceattach --region=asia-southeast1 gcloud compute networks subnets delete psc-nat-subnet --region=asia-southeast1 gcloud compute forwarding-rules delete https-ilb-psc --region=asia-southeast1 gcloud compute addresses delete ilbaddress --region=asia-southeast1 gcloud compute target-https-proxies delete on-premise-httpsproxy --region=asia-southeast1 gcloud compute ssl-certificates delete www01 --region=asia-southeast1 gcloud compute url-maps delete on-premise-url --region=asia-southeast1 gcloud compute backend-services delete on-premise-service-backend --region=asia-southeast1 gcloud compute health-checks delete on-prem-service-hc --region=asia-southeast1 gcloud compute network-endpoint-groups delete on-prem-service-neg --zone=asia-southeast1-b gcloud compute networks subnets delete proxy-subnet-asia-southeast1 --region=asia-southeast1
16. Selamat!
Selamat, Anda telah menyelesaikan codelab.
Yang telah kita bahas
- Load Balancer HTTPS Internal dengan NEG Hybrid dan Health Check Terdistribusi
- Lampiran Layanan PSC dengan Load Balancer HTTPS Internal
- Penyiapan Grup Endpoint Jaringan PSC
- Mengekspos NEG PSC dengan Load Balancer HTTPS Eksternal
