1. Pengantar
Terkadang, workload tidak dapat ditransfer dari database Oracle ke AlloyDB karena berbagai alasan. Dalam kasus tersebut, jika ingin membuat data tersedia di AlloyDB untuk pelaporan atau pemrosesan lebih lanjut, kita dapat memanfaatkan Oracle FDW (Foreign Data Wrapper). Oracle FDW memungkinkan pembuatan kueri data dari database Oracle jarak jauh dan menyajikan data jarak jauh melalui tampilan, membuatnya seolah-olah berada dalam AlloyDB.
Dalam codelab ini, Anda akan mempelajari cara menggunakan FDW Oracle untuk menghubungkan database AlloyDB ke database Oracle yang di-deploy di jaringan terpisah menggunakan layanan VPN.

Diagram di atas menunjukkan cluster AlloyDB dan instance GCE instance-1 di sebelah kiri yang di-deploy di satu VPC dengan jaringan default dan instance GCE ora-xe-01 yang di-deploy di VPC yang berbeda dengan nama jaringan $PROJECT_ID-vpc-02. VPC pertama dan kedua terhubung menggunakan VPN cloud dengan rute yang telah ditetapkan sehingga instance Oracle dan AlloyDB dapat saling berkomunikasi.
AlloyDB ke Oracle melalui VPN AlloyDB ke Oracle melalui VPN
Anda dapat memperoleh informasi selengkapnya tentang ekstensi Oracle FDW di sini.
Prasyarat
- Pemahaman dasar tentang Konsol Google Cloud
- Keterampilan dasar dalam antarmuka command line dan Google Shell
- Pengetahuan dasar tentang database PostgreSQL dan Oracle
Yang akan Anda pelajari
- Cara men-deploy Cluster AlloyDB
- Cara terhubung ke AlloyDB
- Cara mengonfigurasi dan men-deploy contoh database Oracle
- Cara menyiapkan VPN di antara dua jaringan VPC
- Cara mengonfigurasi ekstensi FDW Oracle
Yang Anda butuhkan
- Akun Google Cloud dan Project Google Cloud
- Browser web seperti Chrome
2. Penyiapan dan Persyaratan
Penyiapan lingkungan mandiri
- Login ke Google Cloud Console dan buat project baru atau gunakan kembali project yang sudah ada. Jika belum memiliki akun Gmail atau Google Workspace, Anda harus membuatnya.


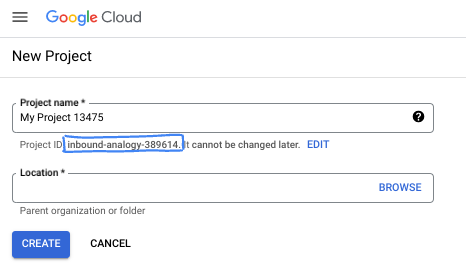
- Project name adalah nama tampilan untuk peserta project ini. String ini adalah string karakter yang tidak digunakan oleh Google API. Anda dapat memperbaruinya kapan saja.
- Project ID bersifat unik di semua project Google Cloud dan tidak dapat diubah (tidak dapat diubah setelah ditetapkan). Cloud Console otomatis membuat string unik; biasanya Anda tidak mementingkan kata-katanya. Di sebagian besar codelab, Anda harus merujuk Project ID-nya (umumnya diidentifikasi sebagai
PROJECT_ID). Jika tidak suka dengan ID yang dibuat, Anda dapat membuat ID acak lainnya. Atau, Anda dapat mencobanya sendiri, dan lihat apakah ID tersebut tersedia. ID tidak dapat diubah setelah langkah ini dan tersedia selama durasi project. - Sebagai informasi, ada nilai ketiga, Project Number, yang digunakan oleh beberapa API. Pelajari lebih lanjut ketiga nilai ini di dokumentasi.
- Selanjutnya, Anda harus mengaktifkan penagihan di Konsol Cloud untuk menggunakan resource/API Cloud. Menjalankan operasi dalam codelab ini tidak akan memakan banyak biaya, bahkan mungkin tidak sama sekali. Guna mematikan resource agar tidak menimbulkan penagihan di luar tutorial ini, Anda dapat menghapus resource yang dibuat atau menghapus project-nya. Pengguna baru Google Cloud memenuhi syarat untuk mengikuti program Uji Coba Gratis senilai $300 USD.
Mulai Cloud Shell
Meskipun Google Cloud dapat dioperasikan dari jarak jauh menggunakan laptop Anda, dalam codelab ini, Anda akan menggunakan Google Cloud Shell, lingkungan command line yang berjalan di Cloud.
Dari Google Cloud Console, klik ikon Cloud Shell di toolbar kanan atas:

Hanya perlu waktu beberapa saat untuk penyediaan dan terhubung ke lingkungan. Jika sudah selesai, Anda akan melihat tampilan seperti ini:

Mesin virtual ini berisi semua alat pengembangan yang Anda perlukan. Layanan ini menawarkan direktori beranda tetap sebesar 5 GB dan beroperasi di Google Cloud, sehingga sangat meningkatkan performa dan autentikasi jaringan. Semua pekerjaan Anda dalam codelab ini dapat dilakukan di browser. Anda tidak perlu menginstal apa pun.
3. Sebelum memulai
Aktifkan API
Output:
Di dalam Cloud Shell, pastikan project ID Anda sudah disiapkan:
gcloud config set project [YOUR-PROJECT-ID]
PROJECT_ID=$(gcloud config get-value project)
Aktifkan semua layanan yang diperlukan:
gcloud services enable alloydb.googleapis.com \
compute.googleapis.com \
cloudresourcemanager.googleapis.com \
servicenetworking.googleapis.com \
vpcaccess.googleapis.com
Output yang diharapkan
student@cloudshell:~ (gleb-test-short-004)$ gcloud services enable alloydb.googleapis.com \
compute.googleapis.com \
cloudresourcemanager.googleapis.com \
servicenetworking.googleapis.com \
vpcaccess.googleapis.com
Operation "operations/acf.p2-404051529011-664c71ad-cb2b-4ab4-86c1-1f3157d70ba1" finished successfully.
Konfigurasi region default Anda ke us-central1 atau region lain yang lebih sesuai untuk Anda. Di lab ini, kita akan menggunakan region us-central1.
gcloud config set compute/region us-central1
4. Deploy Cluster AlloyDB
Sebelum membuat cluster AlloyDB, kita perlu mengalokasikan rentang IP pribadi di VPC untuk digunakan oleh instance AlloyDB mendatang. Setelah itu, kita akan dapat membuat cluster dan instance.
Buat rentang IP pribadi
Kita perlu menyetel konfigurasi Akses Layanan Pribadi di VPC untuk AlloyDB. Asumsinya di sini adalah kita memiliki jaringan VPC "default" dalam project dan jaringan tersebut akan digunakan untuk semua tindakan.
Buat rentang IP pribadi:
gcloud compute addresses create psa-range \
--global \
--purpose=VPC_PEERING \
--prefix-length=16 \
--description="VPC private service access" \
--network=default
Buat koneksi pribadi menggunakan rentang IP yang dialokasikan:
gcloud services vpc-peerings connect \
--service=servicenetworking.googleapis.com \
--ranges=psa-range \
--network=default
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-402417)$ gcloud compute addresses create psa-range \
--global \
--purpose=VPC_PEERING \
--prefix-length=16 \
--description="VPC private service access" \
--network=default
Created [https://www.googleapis.com/compute/v1/projects/test-project-402417/global/addresses/psa-range].
student@cloudshell:~ (test-project-402417)$ gcloud services vpc-peerings connect \
--service=servicenetworking.googleapis.com \
--ranges=psa-range \
--network=default
Operation "operations/pssn.p24-4470404856-595e209f-19b7-4669-8a71-cbd45de8ba66" finished successfully.
student@cloudshell:~ (test-project-402417)$
Buat Cluster AlloyDB
Buat cluster AlloyDB di region default:
export PGPASSWORD=`openssl rand -hex 12`
export REGION=us-central1
export ADBCLUSTER=alloydb-aip-01
gcloud alloydb clusters create $ADBCLUSTER \
--password=$PGPASSWORD \
--network=default \
--region=$REGION
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-402417)$ export PGPASSWORD=`openssl rand -base64 12`
export REGION=us-central1
export ADBCLUSTER=alloydb-aip-01
gcloud alloydb clusters create $ADBCLUSTER \
--password=$PGPASSWORD \
--network=default \
--region=$REGION
Operation ID: operation-1697655441138-6080235852277-9e7f04f5-2012fce4
Creating cluster...done.
Catat sandi PostgreSQL untuk penggunaan berikutnya:
echo $PGPASSWORD
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-402417)$ echo $PGPASSWORD bbefbfde7601985b0dee5723
Buat Instance Utama AlloyDB
Buat instance utama AlloyDB untuk cluster:
export REGION=us-central1
gcloud alloydb instances create $ADBCLUSTER-pr \
--instance-type=PRIMARY \
--cpu-count=2 \
--region=$REGION \
--cluster=$ADBCLUSTER
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-402417)$ gcloud alloydb instances create $ADBCLUSTER-pr \
--instance-type=PRIMARY \
--cpu-count=2 \
--region=$REGION \
--availability-type ZONAL \
--cluster=$ADBCLUSTER
Operation ID: operation-1697659203545-6080315c6e8ee-391805db-25852721
Creating instance...done.
5. Hubungkan ke AlloyDB
Untuk bekerja dengan AlloyDB dan menjalankan perintah seperti buat database, aktifkan ekstensi dan lainnya, kita memerlukan lingkungan pengembangan. Alat ini dapat berupa alat standar apa pun yang berfungsi dengan PostgreSQL. Dalam kasus ini, kami akan menggunakan klien standar untuk PostgreSQL yang diinstal pada kotak {i>linux<i}.
AlloyDB di-deploy menggunakan koneksi khusus pribadi, jadi kita memerlukan VM dengan klien PostgreSQL yang terinstal agar dapat berfungsi dengan database.
Deploy VM GCE
Buat VM GCE di region dan VPC yang sama dengan cluster AlloyDB.
Di Cloud Shell, jalankan:
export ZONE=us-central1-a
gcloud compute instances create instance-1 \
--zone=$ZONE \
--scopes=https://www.googleapis.com/auth/cloud-platform
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-402417)$ export ZONE=us-central1-a
student@cloudshell:~ (test-project-402417)$ gcloud compute instances create instance-1 \
--zone=$ZONE \
--scopes=https://www.googleapis.com/auth/cloud-platform
Created [https://www.googleapis.com/compute/v1/projects/test-project-402417/zones/us-central1-a/instances/instance-1].
NAME: instance-1
ZONE: us-central1-a
MACHINE_TYPE: n1-standard-1
PREEMPTIBLE:
INTERNAL_IP: 10.128.0.2
EXTERNAL_IP: 34.71.192.233
STATUS: RUNNING
Instal Klien Postgres
Instal software klien PostgreSQL pada VM yang di-deploy
Hubungkan ke VM:
gcloud compute ssh instance-1 --zone=us-central1-a
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-402417)$ gcloud compute ssh instance-1 --zone=us-central1-a Updating project ssh metadata...working..Updated [https://www.googleapis.com/compute/v1/projects/test-project-402417]. Updating project ssh metadata...done. Waiting for SSH key to propagate. Warning: Permanently added 'compute.5110295539541121102' (ECDSA) to the list of known hosts. Linux instance-1 5.10.0-26-cloud-amd64 #1 SMP Debian 5.10.197-1 (2023-09-29) x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. student@instance-1:~$
Instal software yang menjalankan perintah dalam VM:
sudo apt-get update
sudo apt-get install --yes postgresql-client
Output konsol yang diharapkan:
student@instance-1:~$ sudo apt-get update sudo apt-get install --yes postgresql-client Get:1 https://packages.cloud.google.com/apt google-compute-engine-bullseye-stable InRelease [5146 B] Get:2 https://packages.cloud.google.com/apt cloud-sdk-bullseye InRelease [6406 B] Hit:3 https://deb.debian.org/debian bullseye InRelease Get:4 https://deb.debian.org/debian-security bullseye-security InRelease [48.4 kB] Get:5 https://packages.cloud.google.com/apt google-compute-engine-bullseye-stable/main amd64 Packages [1930 B] Get:6 https://deb.debian.org/debian bullseye-updates InRelease [44.1 kB] Get:7 https://deb.debian.org/debian bullseye-backports InRelease [49.0 kB] ...redacted... update-alternatives: using /usr/share/postgresql/13/man/man1/psql.1.gz to provide /usr/share/man/man1/psql.1.gz (psql.1.gz) in auto mode Setting up postgresql-client (13+225) ... Processing triggers for man-db (2.9.4-2) ... Processing triggers for libc-bin (2.31-13+deb11u7) ...
Hubungkan ke Instance
Hubungkan ke instance utama dari VM menggunakan psql.
Di tab Cloud Shell yang sama dengan sesi SSH yang terbuka ke instance-1 VM Anda.
Gunakan nilai sandi AlloyDB (PGPASSWORD) yang tercatat dan ID cluster AlloyDB untuk terhubung ke AlloyDB dari VM GCE:
export PGPASSWORD=<Noted password>
ADBCLUSTER=<your AlloyDB cluster name>
REGION=us-central1
INSTANCE_IP=$(gcloud alloydb instances describe $ADBCLUSTER-pr --cluster=$ADBCLUSTER --region=$REGION --format="value(ipAddress)")
export INSTANCE_IP=<AlloyDB Instance IP>
psql "host=$INSTANCE_IP user=postgres sslmode=require"
Output konsol yang diharapkan:
student@instance-1:~$ export PGPASSWORD=CQhOi5OygD4ps6ty
student@instance-1:~$ ADBCLUSTER=alloydb-aip-01
student@instance-1:~$ REGION=us-central1
student@instance-1:~$ INSTANCE_IP=$(gcloud alloydb instances describe $ADBCLUSTER-pr --cluster=$ADBCLUSTER --region=$REGION --format="value(ipAddress)")
gleb@instance-1:~$ psql "host=$INSTANCE_IP user=postgres sslmode=require"
psql (13.13 (Debian 13.13-0+deb11u1), server 14.7)
WARNING: psql major version 13, server major version 14.
Some psql features might not work.
SSL connection (protocol: TLSv1.3, cipher: TLS_AES_256_GCM_SHA384, bits: 256, compression: off)
Type "help" for help.
postgres=>
6. Membuat database Sample Oracle
Contoh database Oracle kami akan di-deploy di VPC terpisah untuk mencerminkan skenario saat di-deploy di infrastruktur lokal atau di lingkungan lain yang terpisah dari VPC cluster AlloyDB.
Membuat VPC Kedua
Menggunakan tab yang terbuka di Cloud Shell atau terminal command line dengan Google Cloud SDK menjalankan:
PROJECT_ID=$(gcloud config get-value project)
REGION=us-central1
gcloud compute networks create $PROJECT_ID-vpc-02 --project=$PROJECT_ID --description=Custom\ VPC\ for\ $PROJECT_ID\ project --subnet-mode=custom --mtu=1460 --bgp-routing-mode=regional
gcloud compute networks subnets create $PROJECT_ID-vpc-02-$REGION --project=$PROJECT_ID --range=10.110.0.0/24 --stack-type=IPV4_ONLY --network=$PROJECT_ID-vpc-02 --region=$REGION
Output konsol yang diharapkan:
student@cloudshell:~ PROJECT_ID=$(gcloud config get-value project) REGION=us-central1 gcloud compute networks create $PROJECT_ID-vpc-02 --project=$PROJECT_ID --description=Custom\ VPC\ for\ $PROJECT_ID\ project --subnet-mode=custom --mtu=1460 --bgp-routing-mode=regional gcloud compute networks subnets create $PROJECT_ID-vpc-02-$REGION --project=$PROJECT_ID --range=10.110.0.0/24 --stack-type=IPV4_ONLY --network=$PROJECT_ID-vpc-02 --region=$REGION Your active configuration is: [cloudshell-3726] Created [https://www.googleapis.com/compute/v1/projects/test-project-402417/global/networks/test-project-402417-vpc-02]. NAME: test-project-402417-vpc-02 SUBNET_MODE: CUSTOM BGP_ROUTING_MODE: REGIONAL IPV4_RANGE: GATEWAY_IPV4: Instances on this network will not be reachable until firewall rules are created. As an example, you can allow all internal traffic between instances as well as SSH, RDP, and ICMP by running: $ gcloud compute firewall-rules create <FIREWALL_NAME> --network test-project-402417-vpc-02 --allow tcp,udp,icmp --source-ranges <IP_RANGE> $ gcloud compute firewall-rules create <FIREWALL_NAME> --network test-project-402417-vpc-02 --allow tcp:22,tcp:3389,icmp Created [https://www.googleapis.com/compute/v1/projects/test-project-402417/regions/us-central1/subnetworks/test-project-402417-vpc-02-us-central1]. NAME: test-project-402417-vpc-02-us-central1 REGION: us-central1 NETWORK: test-project-402417-vpc-02 RANGE: 10.110.0.0/24 STACK_TYPE: IPV4_ONLY IPV6_ACCESS_TYPE:
Konfigurasikan aturan firewall minimum di VPC kedua untuk diagnostik dasar dan koneksi SSH.
gcloud compute firewall-rules create $PROJECT_ID-vpc-02-allow-icmp --project=$PROJECT_ID --network=$PROJECT_ID-vpc-02 --description=Allows\ ICMP\ connections\ from\ any\ source\ to\ any\ instance\ on\ the\ network. --direction=INGRESS --priority=65534 --source-ranges=0.0.0.0/0 --action=ALLOW --rules=icmp
gcloud compute firewall-rules create $PROJECT_ID-vpc-02-allow-ssh --project=$PROJECT_ID --network=$PROJECT_ID-vpc-02 --description=Allows\ TCP\ connections\ from\ any\ source\ to\ any\ instance\ on\ the\ network\ using\ port\ 22. --direction=INGRESS --priority=65534 --source-ranges=0.0.0.0/0 --action=ALLOW --rules=tcp:22
Output konsol yang diharapkan:
student@cloudshell:~ gcloud compute firewall-rules create $PROJECT_ID-vpc-02-allow-icmp --project=$PROJECT_ID --network=$PROJECT_ID-vpc-02 --description=Allows\ ICMP\ connections\ from\ any\ source\ to\ any\ instance\ on\ the\ network. --direction=INGRESS --priority=65534 --source-ranges=0.0.0.0/0 --action=ALLOW --rules=icmp gcloud compute firewall-rules create $PROJECT_ID-vpc-02-allow-ssh --project=$PROJECT_ID --network=$PROJECT_ID-vpc-02 --description=Allows\ TCP\ connections\ from\ any\ source\ to\ any\ instance\ on\ the\ network\ using\ port\ 22. --direction=INGRESS --priority=65534 --source-ranges=0.0.0.0/0 --action=ALLOW --rules=tcp:22 Creating firewall...working..Created [https://www.googleapis.com/compute/v1/projects/test-project-402417/global/firewalls/test-project-402417-vpc-02-allow-icmp]. Creating firewall...done. NAME: test-project-402417-vpc-02-allow-icmp NETWORK: test-project-402417-vpc-02 DIRECTION: INGRESS PRIORITY: 65534 ALLOW: icmp DENY: DISABLED: False Creating firewall...working..Created [https://www.googleapis.com/compute/v1/projects/test-project-402417/global/firewalls/test-project-402417-vpc-02-allow-ssh]. Creating firewall...done. NAME: test-project-402417-vpc-02-allow-ssh NETWORK: test-project-402417-vpc-02 DIRECTION: INGRESS PRIORITY: 65534 ALLOW: tcp:22 DENY: DISABLED: False
Konfigurasikan aturan firewall di default dan VPC kedua untuk mengizinkan koneksi antara subnet internal ke port database.
ALLOYDB_NET_IP_RANGES=$(gcloud compute networks subnets list --network=default --filter="region:us-central1" --format="value(ipCidrRange)"),$(gcloud compute addresses list --filter="name:psa-range AND network:default" --format="value(address_range())")
gcloud compute firewall-rules create default-allow-postgres --project=$PROJECT_ID --network=default --description=Allows\ Postgres\ connections\ from\ local\ networks\ to\ postgres\ instance\ on\ the\ network\ using\ port\ 5432. --direction=INGRESS --priority=65534 --source-ranges=10.110.0.0/24 --action=ALLOW --rules=tcp:5432
gcloud compute firewall-rules create $PROJECT_ID-vpc-02-allow-oracle --project=$PROJECT_ID --network=$PROJECT_ID-vpc-02 --description=Allows\ Oracle\ connections\ from\ local\ networks\ to\ Oracle\ instance\ on\ the\ network\ using\ port\ 1521. --direction=INGRESS --priority=65534 --source-ranges=$ALLOYDB_NET_IP_RANGES --action=ALLOW --rules=tcp:1521
Output konsol yang diharapkan:
student@cloudshell:~ ALLOYDB_NET_IP_RANGES=$(gcloud compute networks subnets list --network=default --filter="region:us-central1" --format="value(ipCidrRange)"),$(gcloud compute addresses list --filter="name:psa-range AND network:default" --format="value(address_range())") gcloud compute firewall-rules create default-allow-postgres --project=$PROJECT_ID --network=default --description=Allows\ Postgres\ connections\ from\ local\ networks\ to\ postgres\ instance\ on\ the\ network\ using\ port\ 5432. --direction=INGRESS --priority=65534 --source-ranges=10.110.0.0/24 --action=ALLOW --rules=tcp:5432 gcloud compute firewall-rules create $PROJECT_ID-vpc-02-allow-oracle --project=$PROJECT_ID --network=$PROJECT_ID-vpc-02 --description=Allows\ Oracle\ connections\ from\ local\ networks\ to\ Oracle\ instance\ on\ the\ network\ using\ port\ 1521. --direction=INGRESS --priority=65534 --source-ranges=$ALLOYDB_NET_IP_RANGES --action=ALLOW --rules=tcp:1521 Creating firewall...working..Created [https://www.googleapis.com/compute/v1/projects/test-project-402417/global/firewalls/default-allow-postgres]. Creating firewall...done. NAME: default-allow-postgres NETWORK: default DIRECTION: INGRESS PRIORITY: 65534 ALLOW: tcp:5432 DENY: DISABLED: False Creating firewall...working..Created [https://www.googleapis.com/compute/v1/projects/test-project-402417/global/firewalls/test-project-402417-vpc-02-allow-oracle]. Creating firewall...done. NAME: test-project-402417-vpc-02-allow-oracle NETWORK: test-project-402417-vpc-02 DIRECTION: INGRESS PRIORITY: 65534 ALLOW: tcp:1521 DENY: DISABLED: False
Deploy VM GCE di VPC kedua
Men-deploy VM GCE menggunakan subnet VPC kedua untuk lingkungan Oracle contoh kami. Instance komputasi ini akan digunakan sebagai lingkungan Oracle pengujian. Biner database Oracle XE akan diinstal di sini dan instance-nya akan digunakan sebagai server serta sebagai klien untuk tugas khusus Oracle.
Dengan menggunakan cloud shell atau terminal yang sama, jalankan perintah untuk membuat VM:
SERVER_NAME=ora-xe-01
PROJECT_ID=$(gcloud config get-value project)
REGION=us-central1
ZONE=us-central1-a
MACHINE_TYPE=e2-standard-2
SUBNET=$PROJECT_ID-vpc-02-$REGION
DISK_SIZE=50
gcloud compute instances create $SERVER_NAME --project=$PROJECT_ID --zone=$ZONE --machine-type=$MACHINE_TYPE --network-interface=subnet=$SUBNET --create-disk=auto-delete=yes,boot=yes,size=$DISK_SIZE,image=projects/debian-cloud/global/images/$(gcloud compute images list --filter="family=debian-11 AND family!=debian-11-arm64" \
--format="value(name)"),type=pd-ssd
Output konsol yang diharapkan:
student@cloudshell:~ SERVER_NAME=ora-xe-01
PROJECT_ID=$(gcloud config get-value project)
REGION=us-central1
ZONE=us-central1-a
MACHINE_TYPE=e2-standard-2
SUBNET=$PROJECT_ID-vpc-02-$REGION
DISK_SIZE=50
gcloud compute instances create $SERVER_NAME --project=$PROJECT_ID --zone=$ZONE --machine-type=$MACHINE_TYPE --network-interface=subnet=$SUBNET --create-disk=auto-delete=yes,boot=yes,size=$DISK_SIZE,image=projects/debian-cloud/global/images/$(gcloud compute images list --filter="family=debian-11 AND family!=debian-11-arm64" \
--format="value(name)"),type=pd-ssd
Your active configuration is: [cloudshell-3726]
Created [https://www.googleapis.com/compute/v1/projects/test-project-402417/zones/us-central1-a/instances/ora-xe-01].
WARNING: Some requests generated warnings:
- Disk size: '50 GB' is larger than image size: '10 GB'. You might need to resize the root repartition manually if the operating system does not support automatic resizing. See https://cloud.google.com/compute/docs/disks/add-persistent-disk#resize_pd for details.
NAME: ora-xe-01
ZONE: us-central1-a
MACHINE_TYPE: e2-standard-2
PREEMPTIBLE:
INTERNAL_IP: 10.110.0.2
EXTERNAL_IP: 34.121.117.216
STATUS: RUNNING
Membuat Oracle XE
Oracle Express Edition (XE) akan digunakan untuk pengujian. Perlu diketahui bahwa penggunaan container Oracle XE tunduk kepada persyaratan lisensi Persyaratan dan Ketentuan Penggunaan Gratis Oracle.
Hubungkan ke VM yang dibuat menggunakan ssh:
gcloud compute ssh $SERVER_NAME --zone=$ZONE
Dalam sesi SSH, deploy paket yang diperlukan untuk jenis Docker dari deployment Oracle XE. Anda dapat membaca opsi deployment lainnya di dokumentasi Oracle.
sudo apt-get update
sudo apt-get -y install ca-certificates curl gnupg lsb-release
sudo mkdir -m 0755 -p /etc/apt/keyrings
curl -fsSL https://download.docker.com/linux/debian/gpg | sudo gpg --dearmor -o /etc/apt/keyrings/docker.gpg
echo "deb [arch=$(dpkg --print-architecture) signed-by=/etc/apt/keyrings/docker.gpg] https://download.docker.com/linux/debian $(lsb_release -cs) stable" | sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
sudo apt-get update
sudo apt-get -y install docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-plugin
sudo usermod -aG docker $USER
Output konsol yang diharapkan (disamarkan):
student@ora-xe-01:~$ sudo apt-get update sudo apt-get -y install ca-certificates curl gnupg lsb-release sudo mkdir -m 0755 -p /etc/apt/keyrings curl -fsSL https://download.docker.com/linux/debian/gpg | sudo gpg --dearmor -o /etc/apt/keyrings/docker.gpg echo "deb [arch=$(dpkg --print-architecture) signed-by=/etc/apt/keyrings/docker.gpg] https://download.docker.com/linux/debian $(lsb_release -cs) stable" | sudo tee /etc/apt/sources.list.d/docker.list > /dev/null sudo apt-get update sudo apt-get -y install docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-plugin sudo usermod -aG docker $USER Get:1 https://packages.cloud.google.com/apt google-compute-engine-bullseye-stable InRelease [5146 B] Get:2 https://packages.cloud.google.com/apt cloud-sdk-bullseye InRelease [6406 B] ... Setting up git (1:2.30.2-1+deb11u2) ... Processing triggers for man-db (2.9.4-2) ... Processing triggers for libc-bin (2.31-13+deb11u7) ... student@ora-xe-01:~$
Hubungkan kembali ke VM dengan logout dan menghubungkan kembali.
exit
gcloud compute ssh $SERVER_NAME --zone=$ZONE
Output konsol yang diharapkan:
student@ora-xe-01:~$ exit logout Connection to 34.132.87.73 closed. student@cloudshell:~ (test-project-002-410214)$ gcloud compute ssh $SERVER_NAME --zone=$ZONE Linux ora-xe-01 5.10.0-26-cloud-amd64 #1 SMP Debian 5.10.197-1 (2023-09-29) x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Thu Jan 4 14:51:25 2024 from 34.73.112.191 student@ora-xe-01:~$
Dalam sesi SSH baru ke ora-xe-01 jalankan:
ORACLE_PWD=`openssl rand -hex 12`
echo $ORACLE_PWD
docker run -d --name oracle-xe -p 1521:1521 -e ORACLE_PWD=$ORACLE_PWD container-registry.oracle.com/database/express:21.3.0-xe
Output konsol yang diharapkan:
student@ora-xe-01:~$ ORACLE_PWD=`openssl rand -hex 12` echo $ORACLE_PWD docker run -d --name oracle-xe -p 1521:1521 -e ORACLE_PWD=$ORACLE_PWD container-registry.oracle.com/database/express:21.3.0-xe e36e191b6c298ce6e02a614c Unable to find image 'container-registry.oracle.com/database/express:21.3.0-xe' locally 21.3.0-xe: Pulling from database/express 2318ff572021: Pull complete c6250726c822: Pull complete 33ac5ea7f7dd: Pull complete 753e0fae7e64: Pull complete Digest: sha256:dcf137aab02d5644aaf9299aae736e4429f9bfdf860676ff398a1458ab8d23f2 Status: Downloaded newer image for container-registry.oracle.com/database/express:21.3.0-xe 9f74e2d37bf49b01785338495e02d79c55c92e4ddd409eddcf45e754fd9044d9
Catat nilai ORACLE_PWD untuk digunakan nanti untuk koneksi ke database sebagai sistem dan sistem pengguna.
Instal Skema Contoh
Buat set data sampel dalam database yang terinstal menggunakan skema sampel sampel HR standar.
Dalam sesi SSH yang sama:
git clone https://github.com/oracle-samples/db-sample-schemas.git
curl -O https://download.oracle.com/otn_software/java/sqldeveloper/sqlcl-latest.zip
sudo apt-get install -y unzip openjdk-17-jdk
unzip sqlcl-latest.zip
echo 'export PATH=$HOME/sqlcl/bin:$PATH' >>.bashrc
exec $SHELL
Output konsol yang diharapkan:
student@ora-xe-01:~$ git clone https://github.com/oracle-samples/db-sample-schemas.git curl -O https://download.oracle.com/otn_software/java/sqldeveloper/sqlcl-latest.zip sudo apt-get install -y unzip openjdk-17-jdk unzip sqlcl-latest.zip echo 'export PATH=$HOME/sqlcl/bin:$PATH' >>.bashrc exec $SHELL Cloning into 'db-sample-schemas'... remote: Enumerating objects: 624, done. remote: Counting objects: 100% (104/104), done. ... inflating: sqlcl/lib/sshd-contrib.jar inflating: sqlcl/lib/sshd-putty.jar inflating: sqlcl/lib/dbtools-sqlcl-distribution.jar student@ora-xe-01:~$
Dalam sesi SSH yang sama:
ORACLE_PWD=<your noted password from the previous step>
cd db-sample-schemas/human_resources/
sql system/$ORACLE_PWD@localhost/XEPDB1 @hr_install.sql
Masukkan sandi untuk skema SDM (sandi yang kuat saja sudah cukup) dan terima ruang tabel default yang disarankan dalam perintah.
Output konsol yang diharapkan:
student@ora-xe-01:~$ ORACLE_PWD=e36e191b6c298ce6e02a614c
student@ora-xe-01:~$ cd db-sample-schemas/human_resources/
sql system/$ORACLE_PWD@localhost/XEPDB1 @hr_install.sql
SQLcl: Release 23.3 Production on Wed Jan 03 14:38:14 2024
Copyright (c) 1982, 2024, Oracle. All rights reserved.
Last Successful login time: Wed Jan 03 2024 14:38:17 +00:00
Connected to:
Oracle Database 21c Express Edition Release 21.0.0.0.0 - Production
Version 21.3.0.0.0
Thank you for installing the Oracle Human Resources Sample Schema.
This installation script will automatically exit your database session
at the end of the installation or if any error is encountered.
The entire installation will be logged into the 'hr_install.log' log file.
Enter a password for the user HR: ************************
Enter a tablespace for HR [USERS]:
Do you want to overwrite the schema, if it already exists? [YES|no]:
****** Creating REGIONS table ....
Table REGIONS created.
...
Table provided actual
______________ ___________ _________
regions 5 5
countries 25 25
departments 27 27
locations 23 23
employees 107 107
jobs 19 19
job_history 10 10
Thank you!
___________________________________________________________
The installation of the sample schema is now finished.
Please check the installation verification output above.
You will now be disconnected from the database.
Thank you for using Oracle Database!
Disconnected from Oracle Database 21c Express Edition Release 21.0.0.0.0 - Production
Version 21.3.0.0.0
Membuat Pengguna untuk FDW Oracle
Untuk mempermudah, kita akan membuat POSTGRES pengguna - sama seperti pengguna PostgreSQL default.
Hubungkan ke database Oracle sebagai pengguna SYS:
sql sys/$ORACLE_PWD@localhost/XEPDB1 as sysdba
Di sesi SQL saat SYS pengguna dieksekusi (ganti POSTGRES_ORA_PWD dengan sandi Anda untuk pengguna):
create user postgres identified by POSTGRES_ORA_PWD;
Dan berikan hak istimewa yang diperlukan kepada pengguna:
grant connect, select any table to postgres;
grant select on v_$SQL_PLAN to postgres;
grant select on v_$SQL to postgres;
Output konsol yang diharapkan:
student@ora-xe-01:~/db-sample-schemas/human_resources$ sql sys/$ORACLE_PWD@localhost/XEPDB1 as sysdba SQLcl: Release 23.3 Production on Wed Jan 03 14:42:37 2024 Copyright (c) 1982, 2024, Oracle. All rights reserved. Connected to: Oracle Database 21c Express Edition Release 21.0.0.0.0 - Production Version 21.3.0.0.0 SQL> create user postgres identified by VeryStrongPassword0011##; User POSTGRES created. SQL> grant connect, select any table to postgres; Grant succeeded. SQL> grant select on v_$SQL_PLAN to postgres; Grant succeeded. SQL> grant select on v_$SQL to postgres; Grant succeeded. SQL>
7. Membuat VPN antar-VPC
Resource yang di-deploy di setiap VPC hanya dapat melihat alamat IP internal untuk jaringan tertentu tersebut dan tidak dapat terhubung ke resource internal apa pun di VPC lain. Google Cloud VPN menciptakan jembatan antara dua VPC dan memungkinkan VM kita dengan database Oracle terhubung dan terhubung dari instance AlloyDB. Koneksi VPN mencakup beberapa komponen, seperti Cloud Router, Gateway, tunnel VPN, dan sesi BGP. Di sini kita akan membahas pembuatan dan konfigurasi semua komponen yang diperlukan untuk mendapatkan VPN dengan ketersediaan tinggi di antara dua VPC. Anda dapat membaca selengkapnya tentang Google Cloud VPN di dokumentasi.
Membuat Router dan Gateway
Membuat Cloud Router dan gateway VPN di kedua VPC.
Di Cloud Shell atau terminal dengan Cloud SDK, jalankan:
PROJECT_ID=$(gcloud config get-value project)
REGION=us-central1
gcloud compute routers create $PROJECT_ID-vpc-01-router --project=$PROJECT_ID --region=$REGION --network=default --asn=64520 --advertisement-mode=custom --set-advertisement-groups=all_subnets
gcloud compute routers create $PROJECT_ID-vpc-02-router --project=$PROJECT_ID --region=$REGION --network=$PROJECT_ID-vpc-02 --asn=64521 --advertisement-mode=custom --set-advertisement-groups=all_subnets
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-402417)$ PROJECT_ID=$(gcloud config get-value project) REGION=us-central1 gcloud compute routers create $PROJECT_ID-vpc-01-router --project=$PROJECT_ID --region=$REGION --network=default --asn=64520 --advertisement-mode=custom --set-advertisement-groups=all_subnets gcloud compute routers create $PROJECT_ID-vpc-02-router --project=$PROJECT_ID --region=$REGION --network=$PROJECT_ID-vpc-02 --asn=64521 --advertisement-mode=custom --set-advertisement-groups=all_subnets Your active configuration is: [cloudshell-18870] Creating router [test-project-402417-vpc-01-router]...done. NAME: test-project-402417-vpc-01-router REGION: us-central1 NETWORK: default Creating router [test-project-402417-vpc-02-router]...done. NAME: test-project-402417-vpc-02-router REGION: us-central1 NETWORK: test-project-402417-vpc-02
Buat gateway VPN di kedua VPC:
PROJECT_ID=$(gcloud config get-value project)
gcloud compute vpn-gateways create $PROJECT_ID-vpc-01-vpn-gtw --project=$PROJECT_ID --region=$REGION --network=default
gcloud compute vpn-gateways create $PROJECT_ID-vpc-02-vpn-gtw --project=$PROJECT_ID --region=$REGION --network=$PROJECT_ID-vpc-02
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-402417)$ gcloud compute vpn-gateways create $PROJECT_ID-vpc-01-vpn-gtw --project=$PROJECT_ID --region=$REGION --network=default gcloud compute vpn-gateways create $PROJECT_ID-vpc-02-vpn-gtw --project=$PROJECT_ID --region=$REGION --network=$PROJECT_ID-vpc-02 Creating VPN Gateway...done. NAME: test-project-402417-vpc-01-vpn-gtw INTERFACE0: 35.242.106.28 INTERFACE1: 35.220.86.122 INTERFACE0_IPV6: INTERFACE1_IPV6: NETWORK: default REGION: us-central1 Creating VPN Gateway...done. NAME: test-project-402417-vpc-02-vpn-gtw INTERFACE0: 35.242.116.197 INTERFACE1: 35.220.68.53 INTERFACE0_IPV6: INTERFACE1_IPV6: NETWORK: test-project-402417-vpc-02 REGION: us-central1 student@cloudshell:~ (test-project-402417)$
Membuat tunnel VPN
Kita akan membuat konfigurasi ketersediaan tinggi (HA) dengan sepasang tunnel VPN untuk setiap VPC.
Di Cloud Shell atau terminal dengan SDK jalankan:
PROJECT_ID=$(gcloud config get-value project)
SHARED_SECRET=`openssl rand -base64 24`
gcloud compute vpn-tunnels create $PROJECT_ID-vpc-01-vpn-tunnel-01 --shared-secret=$SHARED_SECRET --peer-gcp-gateway=$PROJECT_ID-vpc-02-vpn-gtw --ike-version=2 --router=$PROJECT_ID-vpc-01-router --vpn-gateway=$PROJECT_ID-vpc-01-vpn-gtw --project=$PROJECT_ID --region=$REGION --interface=0
gcloud compute vpn-tunnels create $PROJECT_ID-vpc-01-vpn-tunnel-02 --shared-secret=$SHARED_SECRET --peer-gcp-gateway=$PROJECT_ID-vpc-02-vpn-gtw --ike-version=2 --router=$PROJECT_ID-vpc-01-router --vpn-gateway=$PROJECT_ID-vpc-01-vpn-gtw --project=$PROJECT_ID --region=$REGION --interface=1
gcloud compute vpn-tunnels create $PROJECT_ID-vpc-02-vpn-tunnel-01 --shared-secret=$SHARED_SECRET --peer-gcp-gateway=$PROJECT_ID-vpc-01-vpn-gtw --ike-version=2 --router=$PROJECT_ID-vpc-02-router --vpn-gateway=$PROJECT_ID-vpc-02-vpn-gtw --project=$PROJECT_ID --region=$REGION --interface=0
gcloud compute vpn-tunnels create $PROJECT_ID-vpc-02-vpn-tunnel-02 --shared-secret=$SHARED_SECRET --peer-gcp-gateway=$PROJECT_ID-vpc-01-vpn-gtw --ike-version=2 --router=$PROJECT_ID-vpc-02-router --vpn-gateway=$PROJECT_ID-vpc-02-vpn-gtw --project=$PROJECT_ID --region=$REGION --interface=1
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-402417)$ SHARED_SECRET=`openssl rand -base64 24` gcloud compute vpn-tunnels create $PROJECT_ID-vpc-01-vpn-tunnel-01 --shared-secret=$SHARED_SECRET --peer-gcp-gateway=$PROJECT_ID-vpc-02-vpn-gtw --ike-version=2 --router=$PROJECT_ID-vpc-01-router --vpn-gateway=$PROJECT_ID-vpc-01-vpn-gtw --project=$PROJECT_ID --region=$REGION --interface=0 gcloud compute vpn-tunnels create $PROJECT_ID-vpc-01-vpn-tunnel-02 --shared-secret=$SHARED_SECRET --peer-gcp-gateway=$PROJECT_ID-vpc-02-vpn-gtw --ike-version=2 --router=$PROJECT_ID-vpc-01-router --vpn-gateway=$PROJECT_ID-vpc-01-vpn-gtw --project=$PROJECT_ID --region=$REGION --interface=1 gcloud compute vpn-tunnels create $PROJECT_ID-vpc-02-vpn-tunnel-01 --shared-secret=$SHARED_SECRET --peer-gcp-gateway=$PROJECT_ID-vpc-01-vpn-gtw --ike-version=2 --router=$PROJECT_ID-vpc-02-router --vpn-gateway=$PROJECT_ID-vpc-02-vpn-gtw --project=$PROJECT_ID --region=$REGION --interface=0 gcloud compute vpn-tunnels create $PROJECT_ID-vpc-02-vpn-tunnel-02 --shared-secret=$SHARED_SECRET --peer-gcp-gateway=$PROJECT_ID-vpc-01-vpn-gtw --ike-version=2 --router=$PROJECT_ID-vpc-02-router --vpn-gateway=$PROJECT_ID-vpc-02-vpn-gtw --project=$PROJECT_ID --region=$REGION --interface=1 Creating VPN tunnel...done. NAME: test-project-402417-vpc-01-vpn-tunnel-01 REGION: us-central1 GATEWAY: test-project-402417-vpc-01-vpn-gtw VPN_INTERFACE: 0 PEER_ADDRESS: 35.242.116.197 Creating VPN tunnel...done. NAME: test-project-402417-vpc-01-vpn-tunnel-02 REGION: us-central1 GATEWAY: test-project-402417-vpc-01-vpn-gtw VPN_INTERFACE: 1 PEER_ADDRESS: 35.220.68.53 Creating VPN tunnel...done. NAME: test-project-402417-vpc-02-vpn-tunnel-01 REGION: us-central1 GATEWAY: test-project-402417-vpc-02-vpn-gtw VPN_INTERFACE: 0 PEER_ADDRESS: 35.242.106.28 Creating VPN tunnel...done. NAME: test-project-402417-vpc-02-vpn-tunnel-02 REGION: us-central1 GATEWAY: test-project-402417-vpc-02-vpn-gtw VPN_INTERFACE: 1 PEER_ADDRESS: 35.220.86.122
Membuat sesi BGP
Sesi Border Gateway Protocol (BGP) memungkinkan perutean dinamis dengan bertukar informasi tentang rute yang tersedia antar-VPC.
Buat pasangan peer BGP pertama di jaringan (default) pertama. Alamat IP untuk peer akan digunakan untuk BGP yang dibuat di VPC kedua.
Di Cloud Shell atau terminal dengan SDK jalankan:
PROJECT_ID=$(gcloud config get-value project)
gcloud compute routers add-interface $PROJECT_ID-vpc-01-router --interface-name=$PROJECT_ID-vpc-01-router-bgp-if-0 --vpn-tunnel=$PROJECT_ID-vpc-01-vpn-tunnel-01 --region=$REGION
gcloud compute routers add-bgp-peer $PROJECT_ID-vpc-01-router --peer-name=$PROJECT_ID-vpc-01-vpn-tunnel-01-bgp --interface=$PROJECT_ID-vpc-01-router-bgp-if-0 --peer-asn=64521 --region=$REGION
gcloud compute routers add-interface $PROJECT_ID-vpc-01-router --interface-name=$PROJECT_ID-vpc-01-router-bgp-if-1 --vpn-tunnel=$PROJECT_ID-vpc-01-vpn-tunnel-02 --region=$REGION
gcloud compute routers add-bgp-peer $PROJECT_ID-vpc-01-router --peer-name=$PROJECT_ID-vpc-01-vpn-tunnel-02-bgp --interface=$PROJECT_ID-vpc-01-router-bgp-if-1 --peer-asn=64521 --region=$REGION
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-402417)$ gcloud compute routers add-interface $PROJECT_ID-vpc-01-router --interface-name=$PROJECT_ID-vpc-01-router-bgp-if-0 --vpn-tunnel=$PROJECT_ID-vpc-01-vpn-tunnel-01 --region=$REGION gcloud compute routers add-bgp-peer $PROJECT_ID-vpc-01-router --peer-name=$PROJECT_ID-vpc-01-vpn-tunnel-01-bgp --interface=$PROJECT_ID-vpc-01-router-bgp-if-0 --peer-asn=64521 --region=$REGION gcloud compute routers add-interface $PROJECT_ID-vpc-01-router --interface-name=$PROJECT_ID-vpc-01-router-bgp-if-1 --vpn-tunnel=$PROJECT_ID-vpc-01-vpn-tunnel-02 --region=$REGION gcloud compute routers add-bgp-peer $PROJECT_ID-vpc-01-router --peer-name=$PROJECT_ID-vpc-01-vpn-tunnel-02-bgp --interface=$PROJECT_ID-vpc-01-router-bgp-if-1 --peer-asn=64521 --region=$REGION Updated [https://www.googleapis.com/compute/v1/projects/test-project-402417/regions/us-central1/routers/test-project-402417-vpc-01-router]. Creating peer [test-project-402417-vpc-01-vpn-tunnel-01-bgp] in router [test-project-402417-vpc-01-router]...done. Updated [https://www.googleapis.com/compute/v1/projects/test-project-402417/regions/us-central1/routers/test-project-402417-vpc-01-router]. Creating peer [test-project-402417-vpc-01-vpn-tunnel-02-bgp] in router [test-project-402417-vpc-01-router]...done. student@cloudshell:~ (test-project-402417)$
Tambahkan BGP di VPC kedua:
REGION=us-central1
PROJECT_ID=$(gcloud config get-value project)
gcloud compute routers add-interface $PROJECT_ID-vpc-02-router --interface-name=$PROJECT_ID-vpc-02-router-bgp-if-0 --vpn-tunnel=$PROJECT_ID-vpc-02-vpn-tunnel-01 --ip-address=$(gcloud compute routers describe $PROJECT_ID-vpc-01-router --format="value(bgpPeers[0].peerIpAddress)" --region=$REGION) --mask-length=30 --region=$REGION
gcloud compute routers add-bgp-peer $PROJECT_ID-vpc-02-router --peer-name=$PROJECT_ID-vpc-02-vpn-tunnel-01-bgp --interface=$PROJECT_ID-vpc-01-router-bgp-if-0 --peer-ip-address=$(gcloud compute routers describe $PROJECT_ID-vpc-01-router --format="value(bgpPeers[0].ipAddress)" --region=$REGION) --peer-asn=64520 --region=$REGION
gcloud compute routers add-interface $PROJECT_ID-vpc-02-router --interface-name=$PROJECT_ID-vpc-02-router-bgp-if-1 --vpn-tunnel=$PROJECT_ID-vpc-02-vpn-tunnel-02 --ip-address=$(gcloud compute routers describe $PROJECT_ID-vpc-01-router --format="value(bgpPeers[1].peerIpAddress)" --region=$REGION) --mask-length=30 --region=$REGION
gcloud compute routers add-bgp-peer $PROJECT_ID-vpc-02-router --peer-name=$PROJECT_ID-vpc-02-vpn-tunnel-02-bgp --interface=$PROJECT_ID-vpc-01-router-bgp-if-1 --peer-ip-address=$(gcloud compute routers describe $PROJECT_ID-vpc-01-router --format="value(bgpPeers[1].ipAddress)" --region=$REGION) --peer-asn=64520 --region=$REGION
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-402417)$ REGION=us-central1 PROJECT_ID=$(gcloud config get-value project) gcloud compute routers add-interface $PROJECT_ID-vpc-02-router --interface-name=$PROJECT_ID-vpc-02-router-bgp-if-0 --vpn-tunnel=$PROJECT_ID-vpc-02-vpn-tunnel-01 --ip-address=$(gcloud compute routers describe $PROJECT_ID-vpc-01-router --format="value(bgpPeers[0].peerIpAddress)" --region=$REGION) --mask-length=30 --region=$REGION gcloud compute routers add-bgp-peer $PROJECT_ID-vpc-02-router --peer-name=$PROJECT_ID-vpc-02-vpn-tunnel-01-bgp --interface=$PROJECT_ID-vpc-01-router-bgp-if-0 --peer-ip-address=$(gcloud compute routers describe $PROJECT_ID-vpc-01-router --format="value(bgpPeers[0].ipAddress)" --region=$REGION) --peer-asn=64520 --region=$REGION gcloud compute routers add-interface $PROJECT_ID-vpc-02-router --interface-name=$PROJECT_ID-vpc-02-router-bgp-if-1 --vpn-tunnel=$PROJECT_ID-vpc-02-vpn-tunnel-02 --ip-address=$(gcloud compute routers describe $PROJECT_ID-vpc-01-router --format="value(bgpPeers[1].peerIpAddress)" --region=$REGION) --mask-length=30 --region=$REGION gcloud compute routers add-bgp-peer $PROJECT_ID-vpc-02-router --peer-name=$PROJECT_ID-vpc-02-vpn-tunnel-02-bgp --interface=$PROJECT_ID-vpc-01-router-bgp-if-1 --peer-ip-address=$(gcloud compute routers describe $PROJECT_ID-vpc-01-router --format="value(bgpPeers[1].ipAddress)" --region=$REGION) --peer-asn=64520 --region=$REGION Your active configuration is: [cloudshell-18870] Updated [https://www.googleapis.com/compute/v1/projects/test-project-402417/regions/us-central1/routers/test-project-402417-vpc-02-router]. Creating peer [test-project-402417-vpc-02-vpn-tunnel-01-bgp] in router [test-project-402417-vpc-02-router]...done. Updated [https://www.googleapis.com/compute/v1/projects/test-project-402417/regions/us-central1/routers/test-project-402417-vpc-02-router]. Creating peer [test-project-402417-vpc-02-vpn-tunnel-02-bgp] in router [test-project-402417-vpc-02-router]...done.
Menambahkan rute kustom ke BGP
Sekarang kita perlu mengiklankan rentang IP pribadi layanan ke BGP
Di Cloud Shell, jalankan:
PROJECT_ID=$(gcloud config get-value project)
gcloud compute routers update $PROJECT_ID-vpc-01-router --add-advertisement-ranges=$(gcloud compute addresses list --filter="name:psa-range AND network:default" --format="value(address_range())") --region=$REGION
gcloud compute networks peerings update servicenetworking-googleapis-com --network=default --import-custom-routes --export-custom-routes
Output konsol yang diharapkan (disamarkan):
PROJECT_ID=$(gcloud config get-value project) gcloud compute routers update $PROJECT_ID-vpc-01-router --add-advertisement-ranges=$(gcloud compute addresses list --filter="name:psa-range AND network:default" --format="value(address_range())") --region=$REGION gcloud compute networks peerings update servicenetworking-googleapis-com --network=default --import-custom-routes --export-custom-routes ...
8. Mengonfigurasi FDW Oracle di AlloyDB
Sekarang kita dapat membuat database pengujian dan mengonfigurasi ekstensi FDW Oracle. Kita akan menggunakan VM instance-1 yang kita buat pada langkah kedua dan sandi yang dicatat untuk cluster AlloyDB.
Buat Database
Hubungkan ke VM GCE instance-1:
ZONE=us-central1-a
gcloud compute ssh instance-1 --zone=$ZONE
Dalam sesi SSH, jalankan:
export PGPASSWORD=<Noted password>
REGION=us-central1
ADBCLUSTER=alloydb-aip-01
INSTANCE_IP=$(gcloud alloydb instances describe $ADBCLUSTER-pr --cluster=$ADBCLUSTER --region=$REGION --format="value(ipAddress)")
psql "host=$INSTANCE_IP user=postgres" -c "CREATE DATABASE quickstart_db"
Output konsol yang diharapkan:
student@instance-1:~$ export PGPASSWORD=6dd7fKHnMId8RM97 student@instance-1:~$ REGION=us-central1 ADBCLUSTER=alloydb-aip-01 INSTANCE_IP=$(gcloud alloydb instances describe $ADBCLUSTER-pr --cluster=$ADBCLUSTER --region=$REGION --format="value(ipAddress)") psql "host=$INSTANCE_IP user=postgres" -c "CREATE DATABASE quickstart_db" CREATE DATABASE student@instance-1:~$
Mengonfigurasi Ekstensi FDW Oracle
Aktifkan ekstensi FDW Oracle di database yang baru dibuat.
Dalam sesi SSH yang sama, jalankan:
psql -h $INSTANCE_IP -U postgres -d quickstart_db -c "create extension if not exists oracle_fdw cascade"
Output konsol yang diharapkan:
student@instance-1:~$ psql "host=$INSTANCE_IP user=postgres dbname=quickstart_db" -c "create extension if not exists oracle_fdw cascade" CREATE EXTENSION student@instance-1:~$
Mengonfigurasi FDW Oracle
Kami terus mengerjakan sesi SSH yang sama untuk mengonfigurasi Oracle FDW agar berfungsi dengan skema sampel HR di database Oracle.
Buat konfigurasi server FDW menggunakan alamat IP internal untuk VM Oracle XE kami di VPC kedua.
Dalam sesi SSH yang sama dengan instance-1, jalankan:
ORACLE_SERVER_IP=$(gcloud compute instances list --filter="name=(ora-xe-01)" --format="value(networkInterfaces[0].networkIP)")
psql -h $INSTANCE_IP -U postgres -d quickstart_db -c "create server ora_xe foreign data wrapper oracle_fdw options (dbserver '$ORACLE_SERVER_IP:1521/xepdb1')"
Output konsol yang diharapkan:
student@instance-1:~$ ORACLE_SERVER_IP=$(gcloud compute instances list --filter="name=(ora-xe-01)" --format="value(networkInterfaces[0].networkIP)") psql -h $INSTANCE_IP -U postgres -d quickstart_db -c "create server ora_xe foreign data wrapper oracle_fdw options (dbserver '$ORACLE_SERVER_IP:1521/xepdb1')" CREATE SERVER
Berikan penggunaan pada server yang dibuat ke pengguna postgres.
psql -h $INSTANCE_IP -U postgres -d quickstart_db -c "grant usage on foreign server ora_xe to postgres"
Output konsol yang diharapkan:
student@instance-1:~$ psql -h $INSTANCE_IP -U postgres -d quickstart_db -c "grant usage on foreign server ora_xe to postgres" GRANT
Buat pemetaan antara pengguna di PostgreSQL dan pengguna database Oracle menggunakan sandi yang telah kita siapkan untuk pengguna di database Oracle. Gunakan sandi yang telah dibuat untuk pengguna Oracle POSTGRES yang telah kami buat sebelumnya (POSTGRES_ORA_PWD).
POSTGRES_ORA_PWD=<your password for the oracle user postgres>
psql -h $INSTANCE_IP -U postgres -d quickstart_db -c "CREATE USER MAPPING FOR postgres SERVER ora_xe OPTIONS ( USER 'postgres', PASSWORD '$POSTGRES_ORA_PWD')"
Output konsol yang diharapkan:
student@instance-1:~$ POSTGRES_ORA_PWD=VeryStrongPassword0011## student@instance-1:~$ psql -h $INSTANCE_IP -U postgres -d quickstart_db -c "CREATE USER MAPPING FOR postgres SERVER ora_xe OPTIONS ( USER 'postgres', PASSWORD '$POSTGRES_ORA_PWD')" CREATE USER MAPPING
9. Menggunakan Oracle FDW dengan skema HR
Sekarang kita dapat menggunakan FDW Oracle dengan data di database Oracle.
Mengimpor definisi Skema HR Oracle
Kami terus mengerjakan VM klien Postgres menggunakan psql untuk bekerja dengan AlloyDB.
Dalam sesi SSH VM, jalankan:
psql -h $INSTANCE_IP -U postgres -d quickstart_db -c "create schema ora_exe_hr";
psql -h $INSTANCE_IP -U postgres -d quickstart_db -c "import foreign schema \"HR\" from server ora_xe into ora_exe_hr";
Output yang diharapkan (disamarkan):
student@instance-1:~$ psql -h $INSTANCE_IP -U postgres -d quickstart_db -c "create schema ora_exe_hr"; psql -h $INSTANCE_IP -U postgres -d quickstart_db -c "import foreign schema \"HR\" from server ora_xe into ora_exe_hr"; CREATE SCHEMA IMPORT FOREIGN SCHEMA student@instance-1:~$
Menguji FDW Oracle
Mari kita jalankan contoh pernyataan SQL.
Menghubungkan ke database. Dalam sesi SSH VM, jalankan:
psql -h $INSTANCE_IP -U postgres -d quickstart_db
Pada sesi PSQL, jalankan pernyataan {i>select<i}.
select * from ora_exe_hr.countries limit 5;
Output yang diharapkan:
student@instance-1:~$ psql -h $INSTANCE_IP -U postgres -d quickstart_db
psql (13.13 (Debian 13.13-0+deb11u1), server 14.7)
WARNING: psql major version 13, server major version 14.
Some psql features might not work.
SSL connection (protocol: TLSv1.3, cipher: TLS_AES_256_GCM_SHA384, bits: 256, compression: off)
Type "help" for help.
quickstart_db=> select * from ora_exe_hr.countries limit 5;
country_id | country_name | region_id
------------+--------------+-----------
AR | Argentina | 20
AU | Australia | 40
BE | Belgium | 10
BR | Brazil | 20
CA | Canada | 20
(5 rows)
quickstart_db=>
Ini memberikan hasilnya dan itu berarti konfigurasi kita berfungsi dengan benar.
Anda dapat bereksperimen dengan tabel lainnya.
10. Membersihkan lingkungan
Setelah semua tugas selesai, kita bisa membersihkan lingkungan dengan menghancurkan komponen untuk mencegah penagihan yang tidak perlu.
Hancurkan instance dan cluster AlloyDB setelah Anda selesai mengerjakan lab
Hapus cluster AlloyDB dan semua instance
Cluster tersebut dihancurkan dengan opsi paksa yang juga akan menghapus semua instance milik cluster tersebut.
Di Cloud Shell, tentukan variabel project dan lingkungan jika koneksi Anda terputus dan semua setelan sebelumnya hilang:
gcloud config set project <your project id>
export REGION=us-central1
export ADBCLUSTER=alloydb-aip-01
export PROJECT_ID=$(gcloud config get-value project)
Hapus cluster:
gcloud alloydb clusters delete $ADBCLUSTER --region=$REGION --force
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-001-402417)$ gcloud alloydb clusters delete $ADBCLUSTER --region=$REGION --force All of the cluster data will be lost when the cluster is deleted. Do you want to continue (Y/n)? Y Operation ID: operation-1697820178429-6082890a0b570-4a72f7e4-4c5df36f Deleting cluster...done.
Hapus Cadangan AlloyDB
Hapus semua cadangan AlloyDB untuk cluster:
for i in $(gcloud alloydb backups list --filter="CLUSTER_NAME: projects/$PROJECT_ID/locations/$REGION/clusters/$ADBCLUSTER" --format="value(name)" --sort-by=~createTime) ; do gcloud alloydb backups delete $(basename $i) --region $REGION --quiet; done
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-001-402417)$ for i in $(gcloud alloydb backups list --filter="CLUSTER_NAME: projects/$PROJECT_ID/locations/$REGION/clusters/$ADBCLUSTER" --format="value(name)" --sort-by=~createTime) ; do gcloud alloydb backups delete $(basename $i) --region $REGION --quiet; done Operation ID: operation-1697826266108-60829fb7b5258-7f99dc0b-99f3c35f Deleting backup...done.
Sekarang kita bisa menghancurkan VM
Hapus VM GCE
Di Cloud Shell, jalankan:
export GCEVM=instance-1
export ZONE=us-central1-a
gcloud compute instances delete $GCEVM \
--zone=$ZONE \
--quiet
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-001-402417)$ export GCEVM=instance-1
export ZONE=us-central1-a
gcloud compute instances delete $GCEVM \
--zone=$ZONE \
--quiet
Deleted
Menghapus VM dengan Oracle XE
Di Cloud Shell, jalankan:
SERVER_NAME=ora-xe-01
ZONE=us-central1-a
gcloud compute instances delete $SERVER_NAME \
--zone=$ZONE \
--quiet
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-402417)$ SERVER_NAME=ora-xe-01
ZONE=us-central1-a
gcloud compute instances delete $SERVER_NAME \
--zone=$ZONE \
--quiet
Deleted [https://www.googleapis.com/compute/v1/projects/test-project-402417/zones/us-central1-a/instances/ora-xe-01].
student@cloudshell:~ (test-project-402417)$
Hapus VPN
Di Cloud Shell, jalankan:
REGION=us-central1
PROJECT_ID=$(gcloud config get-value project)
gcloud compute vpn-tunnels delete $PROJECT_ID-vpc-01-vpn-tunnel-01 --region=$REGION --quiet
gcloud compute vpn-tunnels delete $PROJECT_ID-vpc-01-vpn-tunnel-02 --region=$REGION --quiet
gcloud compute vpn-tunnels delete $PROJECT_ID-vpc-02-vpn-tunnel-01 --region=$REGION --quiet
gcloud compute vpn-tunnels delete $PROJECT_ID-vpc-02-vpn-tunnel-02 --region=$REGION --quiet
gcloud compute routers delete $PROJECT_ID-vpc-02-router --region=$REGION --quiet
gcloud compute routers delete $PROJECT_ID-vpc-01-router --region=$REGION --quiet
gcloud compute vpn-gateways delete $PROJECT_ID-vpc-01-vpn-gtw --region=$REGION --quiet
gcloud compute vpn-gateways delete $PROJECT_ID-vpc-02-vpn-gtw --region=$REGION --quiet
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-402417)$ REGION=us-central1 PROJECT_ID=$(gcloud config get-value project) gcloud compute vpn-tunnels delete $PROJECT_ID-vpc-01-vpn-tunnel-01 --region=$REGION --quiet gcloud compute vpn-tunnels delete $PROJECT_ID-vpc-01-vpn-tunnel-02 --region=$REGION --quiet gcloud compute vpn-tunnels delete $PROJECT_ID-vpc-02-vpn-tunnel-01 --region=$REGION --quiet gcloud compute vpn-tunnels delete $PROJECT_ID-vpc-02-vpn-tunnel-02 --region=$REGION --quiet gcloud compute routers delete $PROJECT_ID-vpc-02-router --region=$REGION --quiet gcloud compute routers delete $PROJECT_ID-vpc-01-router --region=$REGION --quiet gcloud compute vpn-gateways delete $PROJECT_ID-vpc-01-vpn-gtw --region=$REGION --quiet gcloud compute vpn-gateways delete $PROJECT_ID-vpc-02-vpn-gtw --region=$REGION --quiet Your active configuration is: [cloudshell-18870] Deleting VPN tunnel...done. Deleting VPN tunnel...done. Deleting VPN tunnel...done. Deleting VPN tunnel...done. Deleted [https://www.googleapis.com/compute/v1/projects/test-project-402417/regions/us-central1/routers/test-project-402417-vpc-02-router]. Deleted [https://www.googleapis.com/compute/v1/projects/test-project-402417/regions/us-central1/routers/test-project-402417-vpc-01-router]. Deleting VPN Gateway...done. Deleting VPN Gateway...done. student@cloudshell:~ (test-project-402417)$
Menghapus VPC Kedua
Di Cloud Shell, jalankan:
REGION=us-central1
PROJECT_ID=$(gcloud config get-value project)
gcloud compute firewall-rules delete $PROJECT_ID-vpc-02-allow-icmp --quiet
gcloud compute firewall-rules delete $PROJECT_ID-vpc-02-allow-ssh --quiet
gcloud compute firewall-rules delete default-allow-postgres --quiet
gcloud compute firewall-rules delete $PROJECT_ID-vpc-02-allow-oracle --quiet
gcloud compute networks subnets delete $PROJECT_ID-vpc-02-$REGION --region=$REGION --quiet
gcloud compute networks delete $PROJECT_ID-vpc-02 --quiet
Output konsol yang diharapkan:
student@cloudshell:~ (test-project-402417)$ gcloud compute firewall-rules delete $PROJECT_ID-vpc-02-allow-icmp --quiet gcloud compute firewall-rules delete $PROJECT_ID-vpc-02-allow-ssh --quiet gcloud compute firewall-rules delete default-allow-postgres --quiet gcloud compute firewall-rules delete $PROJECT_ID-vpc-02-allow-oracle --quiet gcloud compute networks subnets delete $PROJECT_ID-vpc-02-$REGION --region=$REGION --quiet gcloud compute networks delete $PROJECT_ID-vpc-02 --quiet Deleted [https://www.googleapis.com/compute/v1/projects/test-project-402417/global/firewalls/test-project-402417-vpc-02-allow-icmp]. Deleted [https://www.googleapis.com/compute/v1/projects/test-project-402417/global/firewalls/test-project-402417-vpc-02-allow-ssh]. Deleted [https://www.googleapis.com/compute/v1/projects/test-project-402417/global/firewalls/default-allow-postgres]. Deleted [https://www.googleapis.com/compute/v1/projects/test-project-402417/global/firewalls/test-project-402417-vpc-02-allow-oracle]. gcloud compute networks subnets delete $PROJECT_ID-vpc-02-$REGION --region=$REGION --quiet gcloud compute networks delete $PROJECT_ID-vpc-02 --quiet
11. Selamat
Selamat, Anda telah menyelesaikan codelab.
Yang telah kita bahas
- Cara men-deploy Cluster AlloyDB
- Cara terhubung ke AlloyDB
- Cara mengonfigurasi dan men-deploy contoh database Oracle
- Cara menyiapkan VPN di antara dua jaringan VPC
- Cara mengonfigurasi ekstensi FDW Oracle
12. Survei
Output:
