1. 簡介
Private Service Connect (PSC) 網路端點群組 (NEG) 支援將內部 HTTPS 負載平衡器與外部 HTTPS 負載平衡器鏈結在一起。依據客戶定義的範圍,提供傳送至地端部署系統的分散式健康狀態檢查和資料層流量。此外,這個拓撲也支援透過多個區域性互連網路連線至地端部署的多個虛擬私有雲。
在本程式碼研究室中,我們會示範如何根據下列拓撲設定這個端對端拓撲設定。從左到右,地端部署客戶的 VM 可模擬 HTTP 服務,利用混合式連線 (HA-VPN 或 InterConnect) 和混合式 NEG 公開,透過內部 HTTPS 負載平衡器公開。PSC 會使用內部 HTTPS 負載平衡器做為服務連結。PSC NEG 會將連結視為後端服務,並向外部 HTTPS LB 公開。網際網路使用者可以運用 Google 全球網路來加快地端部署 HTTP 服務的存取速度。
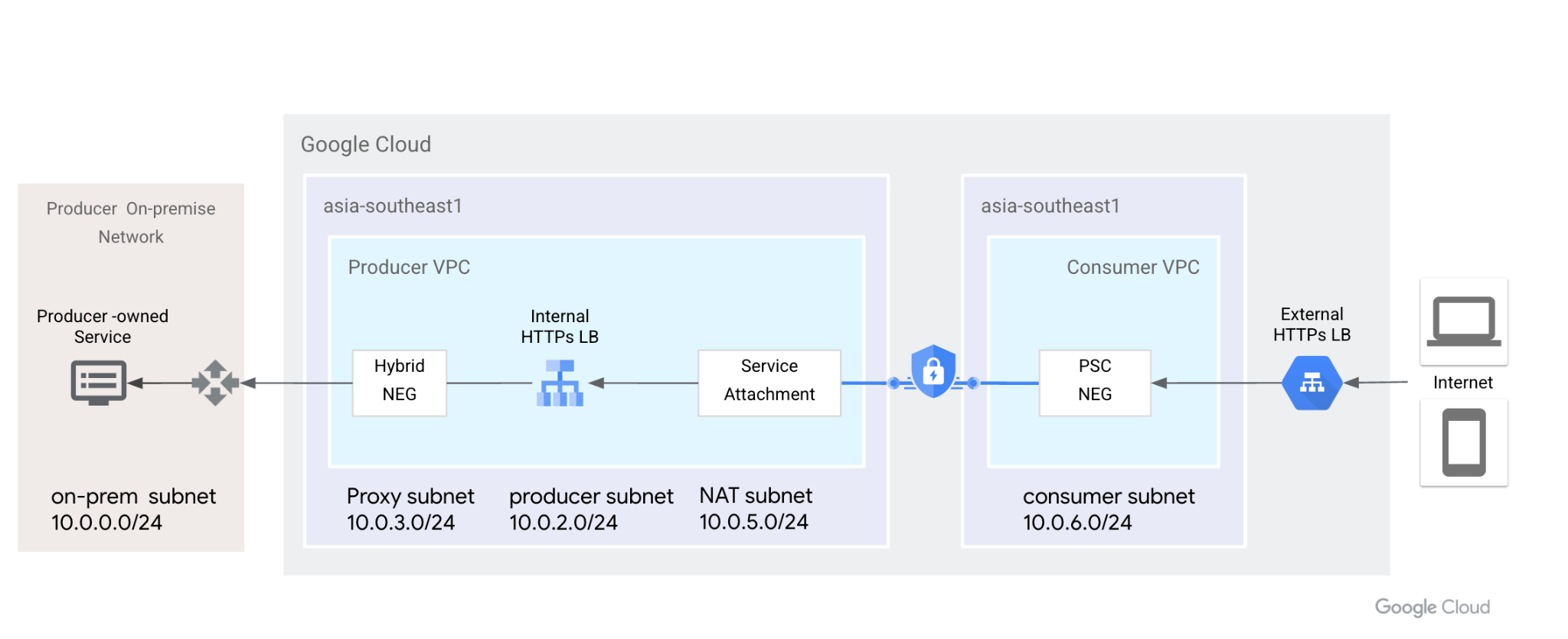
圖 1. Private Service Connect 會使用網路端點群組和服務連結,將外部 HTTPS 負載平衡器連線至內部 HTTPS 負載平衡器,並將後端擴充至地端部署環境。
課程內容
- 採用混合型 NEG 和分散式健康狀態檢查的內部 HTTPS 負載平衡器
- 具有內部 HTTPS 負載平衡器的 PSC 服務連結
- PSC 網路端點群組設定
- 使用外部 HTTPS 負載平衡器公開 PSC NEG
軟硬體需求
- 對高可用性 VPN 等混合式連線有一定程度的瞭解
- 內部/外部 HTTPS 負載平衡的相關知識
- 瞭解 Private Service Connect
2. 事前準備
注意:程式碼研究室會根據圖解的拓撲提供設定和驗證步驟,並依據貴機構的需求修改程序。IAM 權限不在本程式碼研究室的範圍內。
程式碼研究室會使用一項專案模擬整個程序。您也能建立多個專案
單一專案:更新專案,支援生產端和用戶網路
在 Cloud Shell 中,確認您已設定專案 ID
gcloud config list project gcloud config set project [YOUR-PROJECT-NAME] prodproject=YOUR-PROJECT-NAME echo $prodproject
3. 建立地端部署資源
在下一節中,我們會設定地端部署虛擬私有雲和 VM,模擬客戶的地端部署服務。
虛擬私人雲端網路
透過 Cloud Shell
gcloud compute networks create vpc-demo-onprem --project=$prodproject --subnet-mode=custom
建立子網路
透過 Cloud Shell
gcloud compute networks subnets create vpc-demo-onprem-asia-southeast1 --project=$prodproject --range=10.0.0.0/24 --network=vpc-demo-onprem --region=asia-southeast1
建立防火牆規則。
內部 HTTPS 負載平衡器支援分散式健康狀態檢查,防火牆規則只需要允許 Proxy 子網路 IP 範圍。請依照文件將專案加入許可清單。
在 Cloud Shell 中建立防火牆規則,啟用後端健康狀態檢查,以及來自 Proxy 子網路的資料層流量。
gcloud compute firewall-rules create vpc-demo-health-checks --allow tcp:80,tcp:443 --network vpc-demo-onprem --source-ranges 10.0.3.0/24 --enable-logging
在 Cloud Shell 中建立防火牆規則,允許 IAP 連線至您的 VM 執行個體。
gcloud compute firewall-rules create psclab-iap-prod --network vpc-demo-onprem --allow tcp:22 --source-ranges=35.235.240.0/20 --enable-logging
4. 建立地端部署 VM 執行個體
這個 VM 會模擬地端部署服務,並透過混合 NEG 透過內部 HTTPS 負載平衡器公開。
從 Cloud Shell 建立執行個體 www01
gcloud compute instances create www01 \
--zone=asia-southeast1-b \
--image-family=debian-11 \
--image-project=debian-cloud \
--network-interface=network-tier=PREMIUM,nic-type=GVNIC,stack-type=IPV4_ONLY,subnet=vpc-demo-onprem-asia-southeast1 \
--shielded-secure-boot \
--shielded-vtpm \
--shielded-integrity-monitoring \
--metadata=startup-script='#! /bin/bash
sudo apt-get update
sudo apt-get install nginx -y
vm_hostname="$(curl -H "Metadata-Flavor:Google" \
http://169.254.169.254/computeMetadata/v1/instance/name)"
filter="{print \$NF}"
vm_zone="$(curl -H "Metadata-Flavor:Google" \
http://169.254.169.254/computeMetadata/v1/instance/zone \
| awk -F/ "${filter}")"
echo "Page on $vm_hostname in $vm_zone" | \
tee /var/www/html/index.nginx-debian.html
sudo systemctl restart nginx'
在下一節中,我們將使用 letsEncrypt 產生憑證並安裝在 Nginx 上。下載公開金鑰和私密金鑰檔案,進行下一個步驟。需要暫時開啟網際網路的 TCP 通訊埠 80 來產生憑證。
請確定這個 VM 具有公開解析的網域名稱。舉例來說,在 Cloud DNS 中新增 A 記錄 [www01.yinghli.demo.altostrat.com](http://www01.yinghli.demo.altostrat.com) 並指向 VM 公開 IP 位址。
gcloud dns --project=$prodproject record-sets create www01.yinghli.demo.altostrat.com. --zone="yinghli-demo" --type="A" --ttl="300" --rrdatas="34.87.77.186"
從 VM www01 主控台,按照指引在 Nginx 上安裝憑證,並複製 fullchain.pem 和 private.pem 的副本,以進行下列步驟。
sudo apt install snapd sudo snap install core; sudo snap refresh core sudo snap install --classic certbot sudo ln -s /snap/bin/certbot /usr/bin/certbot sudo certbot --nginx
5. 建立生產端虛擬私有雲網路
注意:這項設定「不包含」混合式網路設定。
虛擬私人雲端網路
透過 Cloud Shell
gcloud compute networks create vpc-demo-producer --project=$prodproject --subnet-mode=custom
建立子網路
透過 Cloud Shell
gcloud compute networks subnets create vpc-demo-asia-southeast1 --project=$prodproject --range=10.0.2.0/24 --network=vpc-demo-producer --region=asia-southeast1
建立 Proxy 子網路
透過 Cloud Shell
gcloud compute networks subnets create proxy-subnet-asia-southeast1 \ --purpose=REGIONAL_MANAGED_PROXY \ --role=ACTIVE \ --region=asia-southeast1 \ --network=vpc-demo-producer \ --range=10.0.3.0/24
混合式連線
按照 Cloud VPN 說明文件,在地端部署和生產端虛擬私有雲之間實作高可用性 VPN 連線。保留 Cloud Router 上的預設設定,我們不需要在 BGP 通告中加入 130.211.0.0/22 和 35.191.0.0/16。
6. 建立生產者混合式 NEG
建立混合型網路端點群組,並將地端部署 VM IP:PORT 新增至 NEG。
透過 Cloud Shell
gcloud compute network-endpoint-groups create on-prem-service-neg \
--network-endpoint-type=NON_GCP_PRIVATE_IP_PORT \
--zone=asia-southeast1-b \
--network=vpc-demo-producer
gcloud compute network-endpoint-groups update on-prem-service-neg \
--zone=asia-southeast1-b \
--add-endpoint="ip=10.0.0.2,port=443"
7. 建立生產端內部 HTTPS 負載平衡器
目前外部 HTTPS 負載平衡器僅支援 PSC NEG 的 HTTPS 通訊協定( 說明文件)。已發布的服務時,我們必須使用內部 HTTPS 負載平衡器,並啟用轉送規則的全域存取權。
透過 Cloud Shell 建立地區健康狀態檢查。
gcloud compute health-checks create https on-prem-service-hc \
--region=asia-southeast1 \
--use-serving-port
從 Cloud Shell 建立後端服務,並新增混合式 NEG。
gcloud compute backend-services create on-premise-service-backend \ --load-balancing-scheme=INTERNAL_MANAGED \ --protocol=HTTPS \ --region=asia-southeast1 \ --health-checks=on-prem-service-hc \ --health-checks-region=asia-southeast1 gcloud compute backend-services add-backend on-premise-service-backend \ --network-endpoint-group=on-prem-service-neg \ --network-endpoint-group-zone=asia-southeast1-b \ --region=asia-southeast1 \ --balancing-mode=RATE \ --max-rate-per-endpoint=100
透過 Cloud Shell 建立網址對應
gcloud compute url-maps create on-premise-url \
--default-service on-premise-service-backend \
--region=asia-southeast1
透過 Cloud Shell 建立區域性 SSL 憑證。從 VM 下載兩個憑證檔案。
gcloud compute ssl-certificates create www01 \
--certificate=fullchain.pem \
--private-key=private.pem \
--region=asia-southeast1
透過 Cloud Shell 建立 https-target-proxy
gcloud compute target-https-proxies create on-premise-httpsproxy \
--ssl-certificates=www01 \
--url-map=on-premise-url \
--url-map-region=asia-southeast1 \
--region=asia-southeast1
透過 Cloud Shell 保留內部靜態 IP 並建立轉送規則
gcloud compute addresses create ilbaddress \
--region=asia-southeast1 \
--subnet=vpc-demo-asia-southeast1 \
--addresses=10.0.2.100
gcloud compute forwarding-rules create https-ilb-psc \
--load-balancing-scheme=INTERNAL_MANAGED \
--network=vpc-demo-producer \
--subnet=vpc-demo-asia-southeast1 \
--address=ilbaddress \
--ports=443 \
--region=asia-southeast1 \
--target-https-proxy=on-premise-httpsproxy \
--target-https-proxy-region=asia-southeast1
--allow-global-access
8. 建立生產端 VM 執行個體
請建立生產端 VM 來進行驗證。
透過 Cloud Shell
gcloud compute instances create test01 \
--zone=asia-southeast1-b \
--image-family=debian-11 \
--image-project=debian-cloud \
--network-interface=network-tier=PREMIUM,nic-type=GVNIC,stack-type=IPV4_ONLY,subnet=vpc-demo-asia-southeast1 \
--shielded-secure-boot \
--shielded-vtpm \
--shielded-integrity-monitoring
如要允許 IAP 連線至您的 VM 執行個體,請建立下列防火牆規則:
透過 Cloud Shell
gcloud compute firewall-rules create psclab-iap-prod --network vpc-demo-producer --allow tcp:22 --source-ranges=35.235.240.0/20 --enable-logging
在生產端 VM 控制台中,存取 [www01.yinghli.demo.altostrat.com](https://www01.yinghli.demo.altostrat.com) 並解析內部 HTTPS 負載平衡器 IP 位址。HTTP 200 表示設定可正常運作。
curl -v --resolve www01.yinghli.demo.altostrat.com:443:10.0.2.100 https://www01.yinghli.demo.altostrat.com * Added www01.yinghli.demo.altostrat.com:443:10.0.2.100 to DNS cache * Hostname www01.yinghli.demo.altostrat.com was found in DNS cache * Trying 10.0.2.100:443... * Connected to www01.yinghli.demo.altostrat.com (10.0.2.100) port 443 (#0) * ALPN, offering h2 * ALPN, offering http/1.1 * successfully set certificate verify locations: * CAfile: /etc/ssl/certs/ca-certificates.crt * CApath: /etc/ssl/certs * TLSv1.3 (OUT), TLS handshake, Client hello (1): * TLSv1.3 (IN), TLS handshake, Server hello (2): * TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8): * TLSv1.3 (IN), TLS handshake, Certificate (11): * TLSv1.3 (IN), TLS handshake, CERT verify (15): * TLSv1.3 (IN), TLS handshake, Finished (20): * TLSv1.3 (OUT), TLS change cipher, Change cipher spec (1): * TLSv1.3 (OUT), TLS handshake, Finished (20): * SSL connection using TLSv1.3 / TLS_AES_256_GCM_SHA384 * ALPN, server accepted to use h2 * Server certificate: * subject: CN=www01.yinghli.demo.altostrat.com * start date: Jun 4 10:36:43 2023 GMT * expire date: Sep 2 10:36:42 2023 GMT * subjectAltName: host "www01.yinghli.demo.altostrat.com" matched cert's "www01.yinghli.demo.altostrat.com" * issuer: C=US; O=Let's Encrypt; CN=R3 * SSL certificate verify ok. * Using HTTP2, server supports multi-use * Connection state changed (HTTP/2 confirmed) * Copying HTTP/2 data in stream buffer to connection buffer after upgrade: len=0 * Using Stream ID: 1 (easy handle 0x55865ef982e0) > GET / HTTP/2 > Host: www01.yinghli.demo.altostrat.com > user-agent: curl/7.74.0 > accept: */* > * TLSv1.3 (IN), TLS handshake, Newsession Ticket (4): * TLSv1.3 (IN), TLS handshake, Newsession Ticket (4): * old SSL session ID is stale, removing * Connection state changed (MAX_CONCURRENT_STREAMS == 100)! < HTTP/2 200 < server: nginx/1.18.0 < date: Mon, 05 Jun 2023 02:29:38 GMT < content-type: text/html < content-length: 35 < last-modified: Sun, 04 Jun 2023 09:02:16 GMT < etag: "647c5318-23" < accept-ranges: bytes < via: 1.1 google < Page on www01 in asia-southeast1-b * Connection #0 to host www01.yinghli.demo.altostrat.com left intact
注意:您無法直接存取 VM 10.0.0.2 HTTPS 服務,因為地端部署防火牆僅允許透過 Proxy 子網路 10.0.3.0/24 存取。
9. 建立 PSC NAT 子網路
透過 Cloud Shell
gcloud compute networks subnets create psc-nat-subnet \ --network=vpc-demo-producer \ --region=asia-southeast1 \ --range=10.0.5.0/24 \ --purpose=private-service-connect
10. 建立 HTTPS 服務連結
透過 Cloud Shell 建立 HTTPS 服務連結
gcloud compute service-attachments create ilbserviceattach \ --region=asia-southeast1 \ --producer-forwarding-rule=https-ilb-psc \ --connection-preference=ACCEPT_AUTOMATIC \ --nat-subnets=psc-nat-subnet
驗證 HTTPS 服務連結
gcloud compute service-attachments describe ilbserviceattach --region asia-southeast1
記錄服務連結名稱:
projects/<project>/regions/asia-southeast1/serviceAttachments/ilbserviceattach
11. 建立用戶虛擬私有雲網路
在下一節中,消費者虛擬私有雲在同一個專案中已設定,但也支援不同的專案。用戶端與生產端網路之間的通訊是透過供應商網路中定義的服務連結來完成。
虛擬私人雲端網路
透過 Cloud Shell
gcloud compute networks create vpc-demo-consumer --project=$prodproject --subnet-mode=custom
建立子網路
透過 Cloud Shell
gcloud compute networks subnets create consumer-subnet --project=$prodproject --range=10.0.6.0/24 --network=vpc-demo-consumer --region=asia-southeast1
12. 建立 PSC 網路端點群組
建立 PSC NEG
複製先前的 HTTPS 服務連結名稱,然後貼上參數 --psc-target-service
透過 Cloud Shell
gcloud beta compute network-endpoint-groups create consumerpscneg \ --project=$prodproject \ --region=asia-southeast1 \ --network-endpoint-type=PRIVATE_SERVICE_CONNECT \ --psc-target-service=projects/<project>/regions/asia-southeast1/serviceAttachments/ilbserviceattach \ --network=vpc-demo-consumer \ --subnet=consumer-subnet
成功設定 PSC NEG 後,在使用者介面的 Private Service Connect 之後 ->Published Services ->請注意,已發布的 ilbserviceattach 連線現在會指出 1 項轉送規則。

13. 建立用戶外部 HTTPS 負載平衡器
建立外部 HTTPS 負載平衡器,並將 PSC NEG 做為後端服務( 說明文件)。
透過 Cloud Shell
gcloud compute addresses create httpspsclb \
--ip-version=IPV4 --global
gcloud compute backend-services create consumer-bs \
--load-balancing-scheme=EXTERNAL_MANAGED \
--protocol=HTTPS \
--global
gcloud compute backend-services add-backend consumer-bs \
--network-endpoint-group=consumerpscneg \
--network-endpoint-group-region=asia-southeast1 \
--global
gcloud compute url-maps create consumer-url \
--default-service=consumer-backend-service \
--global
gcloud compute ssl-certificates create wwwglobal \
--certificate=fullchain.pem \
--private-key=private.pem \
--global
gcloud compute target-https-proxies create consumer-url-target-proxy \
--url-map=consumer-url \
--ssl-certificates=wwwglobal
gcloud compute forwarding-rules create consumer-url-forwarding-rule \
--load-balancing-scheme=EXTERNAL_MANAGED \
--network-tier=PREMIUM \
--address=httpspsclb \
--target-https-proxy=consumer-url-target-proxy \
--ports=443 \
--global
更新 www01.yinghli.demo.altostrat.com 的 DNS 記錄,並指向外部 HTTPS 負載平衡器公開 IP 位址
gcloud dns --project=$prodproject record-sets update www01.yinghli.demo.altostrat.com. --type="A" --zone="yinghli-demo" --rrdatas="34.102.178.214" --ttl="300"
14. 驗證
在筆記型電腦上透過 curl 存取 https://www01.yinghli.demo.altostrat.com。
curl -v https://www01.yinghli.demo.altostrat.com * Trying 34.102.178.214:443... * Connected to www01.yinghli.demo.altostrat.com (34.102.178.214) port 443 (#0) * ALPN: offers h2,http/1.1 * TLSv1.3 (OUT), TLS handshake, Client hello (1): * TLSv1.3 (IN), TLS handshake, Server hello (2): * TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8): * TLSv1.3 (IN), TLS handshake, Certificate (11): * TLSv1.3 (IN), TLS handshake, CERT verify (15): * TLSv1.3 (IN), TLS handshake, Finished (20): * TLSv1.3 (OUT), TLS change cipher, Change cipher spec (1): * TLSv1.3 (OUT), TLS handshake, Finished (20): * SSL connection using TLSv1.3 / TLS_AES_256_GCM_SHA384 * ALPN: server accepted h2 * Server certificate: * subject: CN=www01.yinghli.demo.altostrat.com * start date: Jun 4 10:36:43 2023 GMT * expire date: Sep 2 10:36:42 2023 GMT * subjectAltName: host "www01.yinghli.demo.altostrat.com" matched cert's "www01.yinghli.demo.altostrat.com" * issuer: C=US; O=Let's Encrypt; CN=R3 * SSL certificate verify ok. * using HTTP/2 * h2h3 [:method: GET] * h2h3 [:path: /] * h2h3 [:scheme: https] * h2h3 [:authority: www01.yinghli.demo.altostrat.com] * h2h3 [user-agent: curl/8.0.0] * h2h3 [accept: */*] * Using Stream ID: 1 (easy handle 0x149019a00) > GET / HTTP/2 > Host: www01.yinghli.demo.altostrat.com > user-agent: curl/8.0.0 > accept: */* > * TLSv1.3 (IN), TLS handshake, Newsession Ticket (4): * TLSv1.3 (IN), TLS handshake, Newsession Ticket (4): * old SSL session ID is stale, removing < HTTP/2 200 < server: nginx/1.18.0 < date: Mon, 05 Jun 2023 02:48:43 GMT < content-type: text/html < content-length: 35 < last-modified: Sun, 04 Jun 2023 09:02:16 GMT < etag: "647c5318-23" < accept-ranges: bytes < via: 1.1 google, 1.1 google < alt-svc: h3=":443"; ma=2592000,h3-29=":443"; ma=2592000 < Page on www01 in asia-southeast1-b * Connection #0 to host www01.yinghli.demo.altostrat.com left intact
15. 清除步驟
生產端網路清除步驟
注意事項:清除步驟只會顯示負載平衡器和 PSC 相關設定,不含虛擬私有雲和混合式連線。
透過終端機中的單一 Cloud Shell 中的「Delete Lab」元件
gcloud compute forwarding-rules delete consumer-url-forwarding-rule --global gcloud compute target-https-proxies delete consumer-url-target-proxy gcloud compute ssl-certificates delete wwwglobal --global gcloud compute url-maps delete consumer-url gcloud compute backend-services delete consumer-bs --global gcloud compute addresses delete httpspsclb --global gcloud beta compute network-endpoint-groups delete consumerpscneg --region=asia-southeast1 gcloud compute service-attachments delete ilbserviceattach --region=asia-southeast1 gcloud compute networks subnets delete psc-nat-subnet --region=asia-southeast1 gcloud compute forwarding-rules delete https-ilb-psc --region=asia-southeast1 gcloud compute addresses delete ilbaddress --region=asia-southeast1 gcloud compute target-https-proxies delete on-premise-httpsproxy --region=asia-southeast1 gcloud compute ssl-certificates delete www01 --region=asia-southeast1 gcloud compute url-maps delete on-premise-url --region=asia-southeast1 gcloud compute backend-services delete on-premise-service-backend --region=asia-southeast1 gcloud compute health-checks delete on-prem-service-hc --region=asia-southeast1 gcloud compute network-endpoint-groups delete on-prem-service-neg --zone=asia-southeast1-b gcloud compute networks subnets delete proxy-subnet-asia-southeast1 --region=asia-southeast1
16. 恭喜!
恭喜您完成本程式碼研究室。
涵蓋內容
- 採用混合型 NEG 和分散式健康狀態檢查的內部 HTTPS 負載平衡器
- 具有內部 HTTPS 負載平衡器的 PSC 服務連結
- PSC 網路端點群組設定
- 使用外部 HTTPS 負載平衡器公開 PSC NEG
